NotificationThis report is provided "as is" for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise. This document is marked TLP:CLEAR--Disclosure is not limited. Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be distributed without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.cisa.gov/tlp. SummaryDescriptionCISA received 18 files for analysis from a forensic analysis engagement conducted at a Federal Civilian Executive Branch (FCEB) agency. When 11 of the dynamic link library (DLL) files are loaded, the files can read, create, and delete files. If the DLL contains a hardcoded Internet Protocol (IP) address, status messages will be sent to the IP. One DLL file will attempt to collect the target system's Transmission Control Protocol (TCP) connection table, and exfiltrate it to a remote Command and Control server (C2). Five of the files drop and decode a reverse shell utility that can send and receive data and commands. In addition, the files drop and decode an Active Server Pages (ASPX) webshell. Two DLL files are capable of loading and executing payloads. CISA has provided Indicators of Compromise (IOCs) and YARA rules for detection within this Malware Analysis Report (MAR). For more information about this compromise, see Joint Cybersecurity Advisory Threat Actors Exploit Progress Telerik Vulnerability in U.S. Government IIS Server. Download the PDF version of this report: For a downloadable copy of IOCs, see Submitted Files (18)11415ac829c17bd8a9c4cef12c3fbc23095cbb3113c89405e489ead5138384cd (1597974061[.]4531896[.]png) 144492284bcbc0110d34a2b9a44bef90ed0d6cda746df6058b49d3789b0f851d (1666006114[.]5570521[.]txt) 508dd87110cb5bf5d156a13c2430c215035db216f20f546e4acec476e8d55370 (xesmartshell[.]tmp) 707d22cacdbd94a3e6dc884242c0565bdf10a0be42990cd7a5497b124474889b (1665130178[.]9134793[.]dll) 72f7d4d3b9d2e406fa781176bd93e8deee0fb1598b67587e1928455b66b73911 (1594142927[.]995679[.]png) 74544d31cbbf003bc33e7099811f62a37110556b6c1a644393fddd0bac753730 (1665131078[.]6907752[.]dll) 78a926f899320ee6f05ab96f17622fb68e674296689e8649c95f95dade91e933 (1596686310[.]434117[.]png) 833e9cf75079ce796ef60fc7039a0b098be4ce8d259ffa53fe2855df110b2e5d (1665128935[.]8063045[.]dll) 853e8388c9a72a7a54129151884da46075d45a5bcd19c37a7857e268137935aa (1667466391[.]0658665[.]dll) 8a5fc2b8ecb7ac6c0db76049d7e09470dbc24f1a90026a431285244818866505 (1596923477[.]4946315[.]png) a14e2209136dad4f824c6f5986ec5d73d9cc7c86006fd2ceabe34de801062f6b (1665909724[.]4648924[.]dll) b4222cffcdb9fb0eda5aa1703a067021bedd8cf7180cdfc5454d0f07d7eaf18f (1665129315[.]9536858[.]dll) d69ac887ecc2b714b7f5e59e95a4e8ed2466bed753c4ac328931212c46050b35 (1667465147[.]4282858[.]dll) d9273a16f979adee1afb6e55697d3b7ab42fd75051786f8c67a6baf46c4c19c2 (SortVistaCompat) dedf082f523dfcb75dee0480a2d8a087e3231f89fa34fcd2b7f74866a7b6608f (1665214140[.]9324195[.]dll) e044bce06ea49d1eed5e1ec59327316481b8339c3b6e1aecfbb516f56d66e913 (1667465048[.]8995082[.]dll) e45ad91f12188a7c3d4891b70e1ee87a3f23eb981804ea72cd23f1d5e331ff5a (1596835329[.]5015914[.]png) f5cafe99bccb9d813909876fa536cc980c45687d0f411c5f4b5346dcf6b304e4 (1665132690[.]6040645[.]dll) Additional Files (6)08375e2d187ee53ed263ee6529645e03ead1a8e77afd723a3e0495201452d415 (small[.]aspx) 11d8b9be14097614dedd68839c85e3e8feec08cdab675a5e89c5b055a6a68bad (XEReverseShell[.]exe) 1fed0766f564dc05a119bc7fa0b6670f0da23504e23ece94a5ae27787b674cd2 (xesvrs[.]exe) 5cbba90ba539d4eb6097169b0e9acf40b8c4740a01ddb70c67a8fb1fc3524570 (small[.]txt) 815d262d38a26d5695606d03d5a1a49b9c00915ead1d8a2c04eb47846100e93f (XEReverseShell[.]exe) a0ab222673d35d750a0290db1b0ce890b9d40c2ab67bfebb62e1a006e9f2479c (Multi-OS_ReverseShell[.]exe) Domains (3)hivnd[.]com xegroups[.]com xework[.]com IPs (4)137[.]184[.]130[.]162 144[.]96[.]103[.]245 184[.]168[.]104[.]171 45[.]77[.]212[.]12 Findings144492284bcbc0110d34a2b9a44bef90ed0d6cda746df6058b49d3789b0f851dTagswiper Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. This DLL deletes files that end in ".dll" from C:\windows\temp. e044bce06ea49d1eed5e1ec59327316481b8339c3b6e1aecfbb516f56d66e913Tagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Loading this DLL will send "+_+_+" to 45[.]77[.]212[.]12 over port 443. Then, C:\inetpub\temp, D:\inetpub\temp, and E:\inetpub\temp are scanned recursively for files that end in .config. When a .config file is found, the DLL will look for the strings “physicalPath=” and “/>” within the file. If there is data between those two strings, it will be sent to the IP. If there was an error calling CreateFileA, “Errorcode: {Error_Code}” will be sent to the IP. If there was an error calling VirtualAlloc, “VirtualAlloc failed” will be sent to the IP. If there was an error while calling ReadFile, “read file failed” will be sent to the IP. 45[.]77[.]212[.]12Tagscommand-and-control Ports
WhoisNetRange: 45[.]76[.]0[.]0 - 45[.]77[.]255[.]255 OrgName: The Constant Company, LLC OrgNOCHandle: NETWO1159-ARIN OrgAbuseHandle: ABUSE1143-ARIN OrgTechHandle: NETWO1159-ARIN NetRange: 45[.]77[.]212[.]0 - 45[.]77[.]213[.]255 OrgName: Vultr Holdings, LLC OrgAbuseHandle: VULTR-ARIN OrgTechHandle: VULTR-ARIN Relationships
DescriptionThis IP was utilized by multiple malicious applications in this report as a C2 server. It is utilized by the malware to send status information from commands executed on system, as well as a location to exfiltrate sensitive system and network information. d69ac887ecc2b714b7f5e59e95a4e8ed2466bed753c4ac328931212c46050b35Tagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. The file has the same functionality as "1667465048[.]8995082[.]dll" (e044bce06e...). 853e8388c9a72a7a54129151884da46075d45a5bcd19c37a7857e268137935aaTagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Loading this DLL will send "+_+_+" to 45[.]77[.]212[.]12 over port 443. The DLL will then create E:\websites\ Analysis indicates the purpose of this application is to provide a remote operator the ability to determine whether or not they can write files to the system's web server directory. This capability will likely allow the operator to determine whether or not they can remotely install a webshell to allow convenient and persistent remote access to the compromised system. Screenshots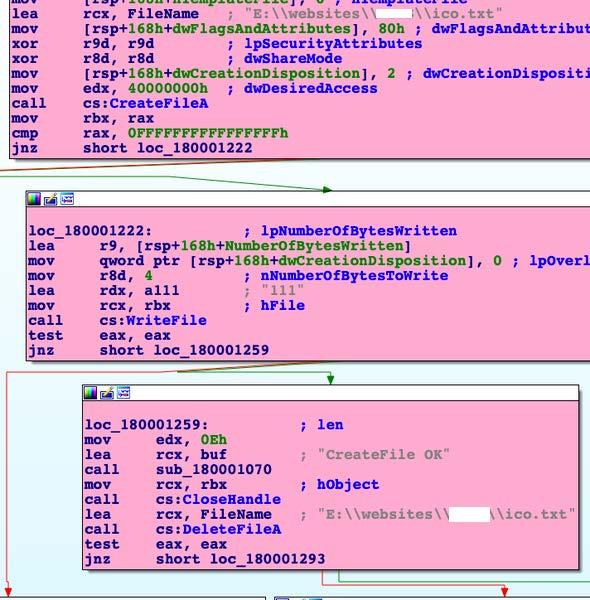 a14e2209136dad4f824c6f5986ec5d73d9cc7c86006fd2ceabe34de801062f6bTagstrojan Details
AntivirusNo matches found. YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Static analysis indicates that the primary purpose of this code is to obtain a copy of the targeted system's TCP connection table via the GetTcpTable API, and export it to the malware's remote C2 server 45[.]77[.]212[.]12. The purpose of this application is to allow a remote operator to determine what systems the targeted system currently has an established TCP session with. This capability will allow the operator to more efficiently profile the targeted network. Screenshots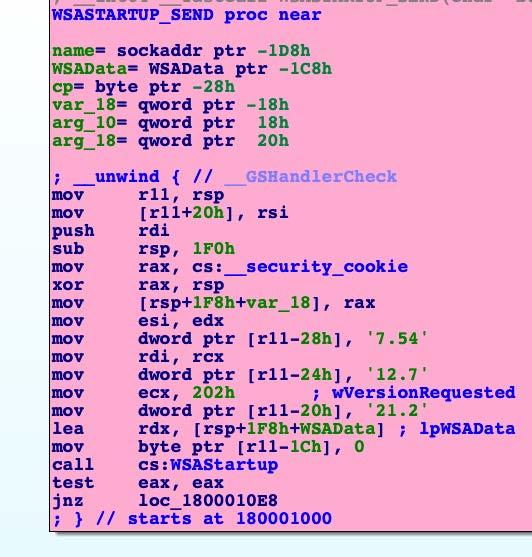 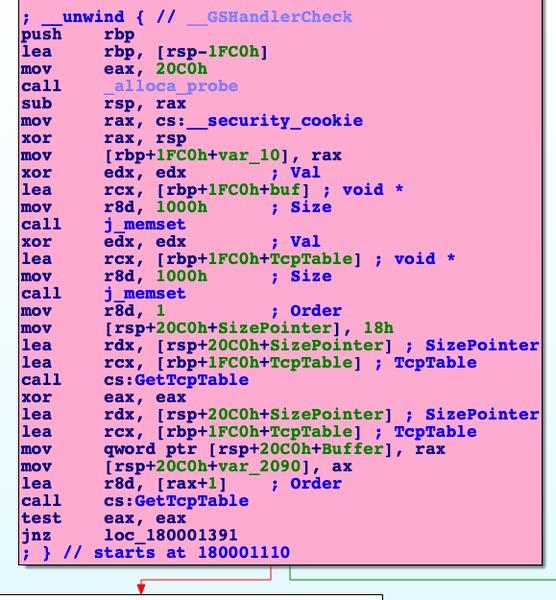 8a5fc2b8ecb7ac6c0db76049d7e09470dbc24f1a90026a431285244818866505Tagsdroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded, it will drop an embedded and base64 encoded payload named ‘sortcombat’ into the path C:\Windows\Temp. The program will then invoke the Windows command-line utility certutil[.]exe with the –decode option and write the new file as sortcombat[.]exe into C:\Windows\Temp. Cmd[.]exe is then invoked to execute sortcombat[.]exe. 11d8b9be14097614dedd68839c85e3e8feec08cdab675a5e89c5b055a6a68badTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility with the internal name of ‘XEReverseShell[.]exe’ that is dropped by "1596923477[.]4946315[.]png" (8a5fc2b8ec...) into C:\Windows\Temp as sortcombat[.]exe. When this utility is executed it will attempt to connect to the domain xework[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Sessions--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XEReverseShell[.]exe will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XEReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain. If it cannot identify the Internet IP address or Reverse Domain the utility attempts to connect to api[.]hackertarget[.]com/reverselookup/?q= to identify the IP address or retrieve answer records for the domain. Api[.]hackertarget[.]com is a legitimate website hosted for blue teams and penetration testers. XEReverseShell will send the system data to the C2 in the following format: ---Begin--- ------------------------[ XE ReverseShell ]----------------------- The utility will expect the command ‘xesetshell’ from the C2. If the command is received it will connect to the C2 and download a file called small[.]txt (5cbba90ba5...). Small[.]txt is a base64 encoded webshell that the program decodes as small[.]aspx and places in the path C:\Windows\Temp. xework[.]comTagscommand-and-control Ports
HTTP Sessions
WhoisDomain Name: XEWORK[.]COM Domain Name: XEWORK[.]COM Relationships
DescriptionAt the time of analysis, the files "XEReverseShell[.]exe" (11d8b9be14...) and "Multi-OS_ReverseShell[.]exe" (a0ab222673...) attempted to connect to this domain. 184[.]168[.]104[.]171Relationships
DescriptionAt the time of analysis, the domains xework[.]com, xegroups[.]com, and hivnd[.]com resolved to this IP address. 144[.]96[.]103[.]245Relationships
DescriptionThe domain xework[.]com returned this IP address as the masterip for the reverse shell. 5cbba90ba539d4eb6097169b0e9acf40b8c4740a01ddb70c67a8fb1fc3524570Tagsdownloaderuploaderwebshell Details
AntivirusNo matches found. YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded text file that is downloaded by "XEReverseShell[.]exe" (11d8b9be14...) and decoded as small[.]aspx. Then it is placed in the path C:\Windows\Temp. 08375e2d187ee53ed263ee6529645e03ead1a8e77afd723a3e0495201452d415Tagsdownloadertrojanuploaderwebshell Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is an ASPX webshell. The webshell is able to enumerate drives on the system, send, receive and delete files, and also execute incoming commands. The webshell contains an interface for easily browsing for files, directories, or drives on the system. It can sort files by size or MAC time, and allows the user to upload or download files to any directory. 78a926f899320ee6f05ab96f17622fb68e674296689e8649c95f95dade91e933Tagsdecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded it will drop an embedded and base64 encoded payload named ‘xesmartshell’ (508dd87110...) into the path C:\Windows\Temp. The program will then invoke certutil[.]exe with the –decode option and write the new file as xesvrs[.]exe (1fed0766f5...) into C:\Windows\Temp. Cmd[.]exe is then invoked to execute the reverse shell. 815d262d38a26d5695606d03d5a1a49b9c00915ead1d8a2c04eb47846100e93fTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘XE ReverseShell[.]exe’ that is dropped and decoded by "1596686310[.]434117[.]png" (78a926f899...). When the utility is executed it will attempt to connect to the domain xegroups[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Session--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XE ReverseShell will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XE ReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain ---Begin--- After the listener is set, the utility will execute the ‘setshell’ command that drops an embedded ASPX webshell (08375e2d18...). If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. xegroups[.]comTagscommand-and-control Ports
HTTP Sessions
WhoisDomain Name: XEGROUPS[.]COM Domain Name: XEGROUPS[.]COM Relationships
DescriptionAt the time of analysis, the files "XEReverseShell[.]exe" (815d262d38...) and "Multi-OS_ReverseShell[.]exe" (1fed0766f56...) attempted to connect to this domain. 508dd87110cb5bf5d156a13c2430c215035db216f20f546e4acec476e8d55370Tagsbackdoordecryptordownloaderdropperloadertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded file. The file will be decoded using the command-line utility certutil[.]exe and executed as xesvrs[.]exe (1fed0766f5...). 1fed0766f564dc05a119bc7fa0b6670f0da23504e23ece94a5ae27787b674cd2Tagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘Multi-OS ReverseShell[.]exe’ that is decoded from xesmartshell[.]tmp (508dd87110...). When the utility is executed it will attempt to connect to the domain xegroups[.]com using Secure Sockets Layer (SSL) to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. Upon receipt of the port number, Multi-OS ReverseShell will establish a listener on the port to accept streamed data. If a port number is not returned, the program will listen on TCP 3979 by default. Multi-OS ReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain ---Begin--- After the listener is set, the utility will execute the ‘setshell’ command that drops an embedded ASPX webshell (08375e2d18...). If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. e45ad91f12188a7c3d4891b70e1ee87a3f23eb981804ea72cd23f1d5e331ff5aTagsdecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded it will drop an embedded and base64 encoded payload named ‘SortVistaCompat’ (d9273a16f9...) into the path C:\Windows\Temp. The program will then invoke the command-line utility certutil[.]exe with the –decode option and write the new file as xesvrs[.]exe (1fed0766f5...) into C:\Windows\Temp. Cmd[.]exe is then invoked to execute the dropped file. d9273a16f979adee1afb6e55697d3b7ab42fd75051786f8c67a6baf46c4c19c2Tagsbackdoordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded file. The file will be decoded using the command-line utility certutil[.]exe and executed as xesvrs[.]exe (1fed0766f5...). a0ab222673d35d750a0290db1b0ce890b9d40c2ab67bfebb62e1a006e9f2479cTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘XEReverseShell[.]exe’ that is dropped by "1596835329[.]5015914[.]png" (e45ad91f12...) into C:\Windows\Temp as xesvrs[.]exe. When the utility is executed it will attempt to connect to the domain xework[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Sessions--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XEReverseShell will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XEReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain. If it cannot identify the Internet IP address or Reverse Domain the utility attempts to connect to api[.]hackertarget[.]com/reverselookup/?q= to identify the IP address or retrieve answer records for the domain. Api[.]hackertarget[.]com is a legitimate website hosted for blue teams and penetration testers. XEReverseShell will send the system data to the C2 in the following format: ------------------------[ XE ReverseShell ]----------------------- ------------------------------------------------------------------------- After the listener is set, the program will drop and decode an embedded base64 encoded webshell named small[.]aspx (08375e2d18...) into the path C:\Windows\Temp. If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. 11415ac829c17bd8a9c4cef12c3fbc23095cbb3113c89405e489ead5138384cdTagsdownloadertrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that is designed to invoke PowerShell to download and execute a file on the system. When the DLL is executed it will attempt to connect to the Uniform Resource Locator (URL) hivnd[.]com/thumpxcache and download a file to the path C:\Windows\Temp. The downloaded file is named thumcache[.]exe and is invoked using cmd[.]exe[.] The file thumcache[.]exe was not available for analysis. hivnd[.]comTagscommand-and-control URLs
Ports
WhoisDomain Name: HIVND[.]COM Domain Name: HIVND[.]COM Relationships
DescriptionAt the time of analysis, the file "1594142927[.]995679[.]png" (11415ac829...) attempted to connect to this domain. 72f7d4d3b9d2e406fa781176bd93e8deee0fb1598b67587e1928455b66b73911Tagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. DescriptionThis artifact is a DLL that is designed to download and execute a payload. The file does not contain a URL to check for downloads. If the program determines that it is running in a virtual environment, it will trigger an exception and terminate. 833e9cf75079ce796ef60fc7039a0b098be4ce8d259ffa53fe2855df110b2e5dTagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This DLL deletes .dll files ending with ".dll" extension in the "C:\windows\temp" directory on the infected machine. This sample also has the capability to enumerate the system, get network parameters including host name, domain name, Domain Name System (DNS) servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, and Dynamic Host Configuration Protocol (DHCP) server. The sample then communicates the collected data to a C2 server located at IP address 137[.]184[.]130[.]162. 137[.]184[.]130[.]162Tagscommand-and-control Ports
WhoisNetRange: 137[.]184[.]0[.]0 - 137[.]184[.]255[.]255 OrgName: DigitalOcean, LLC OrgAbuseHandle: ABUSE5232-ARIN OrgTechHandle: NOC32014-ARIN OrgNOCHandle: NOC32014-ARIN Relationships
DescriptionThis IP address is the C2 server that the samples connect to. b4222cffcdb9fb0eda5aa1703a067021bedd8cf7180cdfc5454d0f07d7eaf18fTagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This sample has the capability to load additional libraries, enumerate the system, processes, files, directories, and has the ability to write files, get network parameters including host name, domain name, DNS servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, and DHCP server. The sample then communicates the collected data to a C2 server located at IP address 137[.]184[.]130[.]162. 707d22cacdbd94a3e6dc884242c0565bdf10a0be42990cd7a5497b124474889bTagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This sample has capability to get network parameters including host name, domain name, DNS servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, DHCP server, and additional data and communicate it to a C2 server located at IP address 137[.]184[.]130[.]162 over port 443. 74544d31cbbf003bc33e7099811f62a37110556b6c1a644393fddd0bac753730Tagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...). f5cafe99bccb9d813909876fa536cc980c45687d0f411c5f4b5346dcf6b304e4Tagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...). dedf082f523dfcb75dee0480a2d8a087e3231f89fa34fcd2b7f74866a7b6608fTagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...), except it does not have the capability for network communication. However, the IP address 137[.]184[.]130[.]164 is hard-coded within the sample like the other files. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. Please share your thoughts. We recently updated our anonymous Product Feedback Survey and we'd welcome your feedback. |
https://www.cisa.gov/news-events/analysis-reports/ar23-074a
NotificationThis report is provided "as is" for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise. This document is marked TLP:CLEAR--Disclosure is not limited. Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be distributed without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.cisa.gov/tlp. SummaryDescriptionCISA received 18 files for analysis from a forensic analysis engagement conducted at a Federal Civilian Executive Branch (FCEB) agency. When 11 of the dynamic link library (DLL) files are loaded, the files can read, create, and delete files. If the DLL contains a hardcoded Internet Protocol (IP) address, status messages will be sent to the IP. One DLL file will attempt to collect the target system's Transmission Control Protocol (TCP) connection table, and exfiltrate it to a remote Command and Control server (C2). Five of the files drop and decode a reverse shell utility that can send and receive data and commands. In addition, the files drop and decode an Active Server Pages (ASPX) webshell. Two DLL files are capable of loading and executing payloads. CISA has provided Indicators of Compromise (IOCs) and YARA rules for detection within this Malware Analysis Report (MAR). For more information about this compromise, see Joint Cybersecurity Advisory Threat Actors Exploit Progress Telerik Vulnerability in U.S. Government IIS Server. Download the PDF version of this report: For a downloadable copy of IOCs, see Submitted Files (18)11415ac829c17bd8a9c4cef12c3fbc23095cbb3113c89405e489ead5138384cd (1597974061[.]4531896[.]png) 144492284bcbc0110d34a2b9a44bef90ed0d6cda746df6058b49d3789b0f851d (1666006114[.]5570521[.]txt) 508dd87110cb5bf5d156a13c2430c215035db216f20f546e4acec476e8d55370 (xesmartshell[.]tmp) 707d22cacdbd94a3e6dc884242c0565bdf10a0be42990cd7a5497b124474889b (1665130178[.]9134793[.]dll) 72f7d4d3b9d2e406fa781176bd93e8deee0fb1598b67587e1928455b66b73911 (1594142927[.]995679[.]png) 74544d31cbbf003bc33e7099811f62a37110556b6c1a644393fddd0bac753730 (1665131078[.]6907752[.]dll) 78a926f899320ee6f05ab96f17622fb68e674296689e8649c95f95dade91e933 (1596686310[.]434117[.]png) 833e9cf75079ce796ef60fc7039a0b098be4ce8d259ffa53fe2855df110b2e5d (1665128935[.]8063045[.]dll) 853e8388c9a72a7a54129151884da46075d45a5bcd19c37a7857e268137935aa (1667466391[.]0658665[.]dll) 8a5fc2b8ecb7ac6c0db76049d7e09470dbc24f1a90026a431285244818866505 (1596923477[.]4946315[.]png) a14e2209136dad4f824c6f5986ec5d73d9cc7c86006fd2ceabe34de801062f6b (1665909724[.]4648924[.]dll) b4222cffcdb9fb0eda5aa1703a067021bedd8cf7180cdfc5454d0f07d7eaf18f (1665129315[.]9536858[.]dll) d69ac887ecc2b714b7f5e59e95a4e8ed2466bed753c4ac328931212c46050b35 (1667465147[.]4282858[.]dll) d9273a16f979adee1afb6e55697d3b7ab42fd75051786f8c67a6baf46c4c19c2 (SortVistaCompat) dedf082f523dfcb75dee0480a2d8a087e3231f89fa34fcd2b7f74866a7b6608f (1665214140[.]9324195[.]dll) e044bce06ea49d1eed5e1ec59327316481b8339c3b6e1aecfbb516f56d66e913 (1667465048[.]8995082[.]dll) e45ad91f12188a7c3d4891b70e1ee87a3f23eb981804ea72cd23f1d5e331ff5a (1596835329[.]5015914[.]png) f5cafe99bccb9d813909876fa536cc980c45687d0f411c5f4b5346dcf6b304e4 (1665132690[.]6040645[.]dll) Additional Files (6)08375e2d187ee53ed263ee6529645e03ead1a8e77afd723a3e0495201452d415 (small[.]aspx) 11d8b9be14097614dedd68839c85e3e8feec08cdab675a5e89c5b055a6a68bad (XEReverseShell[.]exe) 1fed0766f564dc05a119bc7fa0b6670f0da23504e23ece94a5ae27787b674cd2 (xesvrs[.]exe) 5cbba90ba539d4eb6097169b0e9acf40b8c4740a01ddb70c67a8fb1fc3524570 (small[.]txt) 815d262d38a26d5695606d03d5a1a49b9c00915ead1d8a2c04eb47846100e93f (XEReverseShell[.]exe) a0ab222673d35d750a0290db1b0ce890b9d40c2ab67bfebb62e1a006e9f2479c (Multi-OS_ReverseShell[.]exe) Domains (3)hivnd[.]com xegroups[.]com xework[.]com IPs (4)137[.]184[.]130[.]162 144[.]96[.]103[.]245 184[.]168[.]104[.]171 45[.]77[.]212[.]12 Findings144492284bcbc0110d34a2b9a44bef90ed0d6cda746df6058b49d3789b0f851dTagswiper Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. This DLL deletes files that end in ".dll" from C:\windows\temp. e044bce06ea49d1eed5e1ec59327316481b8339c3b6e1aecfbb516f56d66e913Tagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Loading this DLL will send "+_+_+" to 45[.]77[.]212[.]12 over port 443. Then, C:\inetpub\temp, D:\inetpub\temp, and E:\inetpub\temp are scanned recursively for files that end in .config. When a .config file is found, the DLL will look for the strings “physicalPath=” and “/>” within the file. If there is data between those two strings, it will be sent to the IP. If there was an error calling CreateFileA, “Errorcode: {Error_Code}” will be sent to the IP. If there was an error calling VirtualAlloc, “VirtualAlloc failed” will be sent to the IP. If there was an error while calling ReadFile, “read file failed” will be sent to the IP. 45[.]77[.]212[.]12Tagscommand-and-control Ports
WhoisNetRange: 45[.]76[.]0[.]0 - 45[.]77[.]255[.]255 OrgName: The Constant Company, LLC OrgNOCHandle: NETWO1159-ARIN OrgAbuseHandle: ABUSE1143-ARIN OrgTechHandle: NETWO1159-ARIN NetRange: 45[.]77[.]212[.]0 - 45[.]77[.]213[.]255 OrgName: Vultr Holdings, LLC OrgAbuseHandle: VULTR-ARIN OrgTechHandle: VULTR-ARIN Relationships
DescriptionThis IP was utilized by multiple malicious applications in this report as a C2 server. It is utilized by the malware to send status information from commands executed on system, as well as a location to exfiltrate sensitive system and network information. d69ac887ecc2b714b7f5e59e95a4e8ed2466bed753c4ac328931212c46050b35Tagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. The file has the same functionality as "1667465048[.]8995082[.]dll" (e044bce06e...). 853e8388c9a72a7a54129151884da46075d45a5bcd19c37a7857e268137935aaTagsinformation-stealer Details
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Loading this DLL will send "+_+_+" to 45[.]77[.]212[.]12 over port 443. The DLL will then create E:\websites\ Analysis indicates the purpose of this application is to provide a remote operator the ability to determine whether or not they can write files to the system's web server directory. This capability will likely allow the operator to determine whether or not they can remotely install a webshell to allow convenient and persistent remote access to the compromised system. Screenshots a14e2209136dad4f824c6f5986ec5d73d9cc7c86006fd2ceabe34de801062f6bTagstrojan Details
AntivirusNo matches found. YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a malicious .NET DLL, which contains malicious unmanaged 64-bit Intel code. Static analysis indicates that the primary purpose of this code is to obtain a copy of the targeted system's TCP connection table via the GetTcpTable API, and export it to the malware's remote C2 server 45[.]77[.]212[.]12. The purpose of this application is to allow a remote operator to determine what systems the targeted system currently has an established TCP session with. This capability will allow the operator to more efficiently profile the targeted network. Screenshots  8a5fc2b8ecb7ac6c0db76049d7e09470dbc24f1a90026a431285244818866505Tagsdroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded, it will drop an embedded and base64 encoded payload named ‘sortcombat’ into the path C:\Windows\Temp. The program will then invoke the Windows command-line utility certutil[.]exe with the –decode option and write the new file as sortcombat[.]exe into C:\Windows\Temp. Cmd[.]exe is then invoked to execute sortcombat[.]exe. 11d8b9be14097614dedd68839c85e3e8feec08cdab675a5e89c5b055a6a68badTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility with the internal name of ‘XEReverseShell[.]exe’ that is dropped by "1596923477[.]4946315[.]png" (8a5fc2b8ec...) into C:\Windows\Temp as sortcombat[.]exe. When this utility is executed it will attempt to connect to the domain xework[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Sessions--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XEReverseShell[.]exe will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XEReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain. If it cannot identify the Internet IP address or Reverse Domain the utility attempts to connect to api[.]hackertarget[.]com/reverselookup/?q= to identify the IP address or retrieve answer records for the domain. Api[.]hackertarget[.]com is a legitimate website hosted for blue teams and penetration testers. XEReverseShell will send the system data to the C2 in the following format: ---Begin--- ------------------------[ XE ReverseShell ]----------------------- The utility will expect the command ‘xesetshell’ from the C2. If the command is received it will connect to the C2 and download a file called small[.]txt (5cbba90ba5...). Small[.]txt is a base64 encoded webshell that the program decodes as small[.]aspx and places in the path C:\Windows\Temp. xework[.]comTagscommand-and-control Ports
HTTP Sessions
WhoisDomain Name: XEWORK[.]COM Domain Name: XEWORK[.]COM Relationships
DescriptionAt the time of analysis, the files "XEReverseShell[.]exe" (11d8b9be14...) and "Multi-OS_ReverseShell[.]exe" (a0ab222673...) attempted to connect to this domain. 184[.]168[.]104[.]171Relationships
DescriptionAt the time of analysis, the domains xework[.]com, xegroups[.]com, and hivnd[.]com resolved to this IP address. 144[.]96[.]103[.]245Relationships
DescriptionThe domain xework[.]com returned this IP address as the masterip for the reverse shell. 5cbba90ba539d4eb6097169b0e9acf40b8c4740a01ddb70c67a8fb1fc3524570Tagsdownloaderuploaderwebshell Details
AntivirusNo matches found. YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded text file that is downloaded by "XEReverseShell[.]exe" (11d8b9be14...) and decoded as small[.]aspx. Then it is placed in the path C:\Windows\Temp. 08375e2d187ee53ed263ee6529645e03ead1a8e77afd723a3e0495201452d415Tagsdownloadertrojanuploaderwebshell Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is an ASPX webshell. The webshell is able to enumerate drives on the system, send, receive and delete files, and also execute incoming commands. The webshell contains an interface for easily browsing for files, directories, or drives on the system. It can sort files by size or MAC time, and allows the user to upload or download files to any directory. 78a926f899320ee6f05ab96f17622fb68e674296689e8649c95f95dade91e933Tagsdecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded it will drop an embedded and base64 encoded payload named ‘xesmartshell’ (508dd87110...) into the path C:\Windows\Temp. The program will then invoke certutil[.]exe with the –decode option and write the new file as xesvrs[.]exe (1fed0766f5...) into C:\Windows\Temp. Cmd[.]exe is then invoked to execute the reverse shell. 815d262d38a26d5695606d03d5a1a49b9c00915ead1d8a2c04eb47846100e93fTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘XE ReverseShell[.]exe’ that is dropped and decoded by "1596686310[.]434117[.]png" (78a926f899...). When the utility is executed it will attempt to connect to the domain xegroups[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Session--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XE ReverseShell will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XE ReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain ---Begin--- After the listener is set, the utility will execute the ‘setshell’ command that drops an embedded ASPX webshell (08375e2d18...). If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. xegroups[.]comTagscommand-and-control Ports
HTTP Sessions
WhoisDomain Name: XEGROUPS[.]COM Domain Name: XEGROUPS[.]COM Relationships
DescriptionAt the time of analysis, the files "XEReverseShell[.]exe" (815d262d38...) and "Multi-OS_ReverseShell[.]exe" (1fed0766f56...) attempted to connect to this domain. 508dd87110cb5bf5d156a13c2430c215035db216f20f546e4acec476e8d55370Tagsbackdoordecryptordownloaderdropperloadertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded file. The file will be decoded using the command-line utility certutil[.]exe and executed as xesvrs[.]exe (1fed0766f5...). 1fed0766f564dc05a119bc7fa0b6670f0da23504e23ece94a5ae27787b674cd2Tagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘Multi-OS ReverseShell[.]exe’ that is decoded from xesmartshell[.]tmp (508dd87110...). When the utility is executed it will attempt to connect to the domain xegroups[.]com using Secure Sockets Layer (SSL) to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. Upon receipt of the port number, Multi-OS ReverseShell will establish a listener on the port to accept streamed data. If a port number is not returned, the program will listen on TCP 3979 by default. Multi-OS ReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain ---Begin--- After the listener is set, the utility will execute the ‘setshell’ command that drops an embedded ASPX webshell (08375e2d18...). If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. e45ad91f12188a7c3d4891b70e1ee87a3f23eb981804ea72cd23f1d5e331ff5aTagsdecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that drops and executes a reverse shell utility. When the DLL is loaded it will drop an embedded and base64 encoded payload named ‘SortVistaCompat’ (d9273a16f9...) into the path C:\Windows\Temp. The program will then invoke the command-line utility certutil[.]exe with the –decode option and write the new file as xesvrs[.]exe (1fed0766f5...) into C:\Windows\Temp. Cmd[.]exe is then invoked to execute the dropped file. d9273a16f979adee1afb6e55697d3b7ab42fd75051786f8c67a6baf46c4c19c2Tagsbackdoordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a base64 encoded file. The file will be decoded using the command-line utility certutil[.]exe and executed as xesvrs[.]exe (1fed0766f5...). a0ab222673d35d750a0290db1b0ce890b9d40c2ab67bfebb62e1a006e9f2479cTagsbackdoordecryptordroppertrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a reverse shell utility named ‘XEReverseShell[.]exe’ that is dropped by "1596835329[.]5015914[.]png" (e45ad91f12...) into C:\Windows\Temp as xesvrs[.]exe. When the utility is executed it will attempt to connect to the domain xework[.]com to obtain the IP address of the C2 and port number to listen on. If no IP address or port number is obtained the program will terminate. ---Begin HTTP Sessions--- GET /masterport HTTP/1[.]1 Upon receipt of the port number, XEReverseShell will establish a listener on the port to accept streamed data. The utility is able to read or write streamed data and pass incoming commands to a command shell. XEReverseShell collects the path to the web server system files, current username, APP_POOL (IIS Application Pool configuration), ComputerName, OSVersion, Internet IP, Local IP and Reverse Domain. If it cannot identify the Internet IP address or Reverse Domain the utility attempts to connect to api[.]hackertarget[.]com/reverselookup/?q= to identify the IP address or retrieve answer records for the domain. Api[.]hackertarget[.]com is a legitimate website hosted for blue teams and penetration testers. XEReverseShell will send the system data to the C2 in the following format: ------------------------[ XE ReverseShell ]----------------------- ------------------------------------------------------------------------- After the listener is set, the program will drop and decode an embedded base64 encoded webshell named small[.]aspx (08375e2d18...) into the path C:\Windows\Temp. If the utility receives the command ‘xequit’ it will sleep for a period of time determined by the adversary. 11415ac829c17bd8a9c4cef12c3fbc23095cbb3113c89405e489ead5138384cdTagsdownloadertrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis artifact is a DLL that is designed to invoke PowerShell to download and execute a file on the system. When the DLL is executed it will attempt to connect to the Uniform Resource Locator (URL) hivnd[.]com/thumpxcache and download a file to the path C:\Windows\Temp. The downloaded file is named thumcache[.]exe and is invoked using cmd[.]exe[.] The file thumcache[.]exe was not available for analysis. hivnd[.]comTagscommand-and-control URLs
Ports
WhoisDomain Name: HIVND[.]COM Domain Name: HIVND[.]COM Relationships
DescriptionAt the time of analysis, the file "1594142927[.]995679[.]png" (11415ac829...) attempted to connect to this domain. 72f7d4d3b9d2e406fa781176bd93e8deee0fb1598b67587e1928455b66b73911Tagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. DescriptionThis artifact is a DLL that is designed to download and execute a payload. The file does not contain a URL to check for downloads. If the program determines that it is running in a virtual environment, it will trigger an exception and terminate. 833e9cf75079ce796ef60fc7039a0b098be4ce8d259ffa53fe2855df110b2e5dTagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This DLL deletes .dll files ending with ".dll" extension in the "C:\windows\temp" directory on the infected machine. This sample also has the capability to enumerate the system, get network parameters including host name, domain name, Domain Name System (DNS) servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, and Dynamic Host Configuration Protocol (DHCP) server. The sample then communicates the collected data to a C2 server located at IP address 137[.]184[.]130[.]162. 137[.]184[.]130[.]162Tagscommand-and-control Ports
WhoisNetRange: 137[.]184[.]0[.]0 - 137[.]184[.]255[.]255 OrgName: DigitalOcean, LLC OrgAbuseHandle: ABUSE5232-ARIN OrgTechHandle: NOC32014-ARIN OrgNOCHandle: NOC32014-ARIN Relationships
DescriptionThis IP address is the C2 server that the samples connect to. b4222cffcdb9fb0eda5aa1703a067021bedd8cf7180cdfc5454d0f07d7eaf18fTagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This sample has the capability to load additional libraries, enumerate the system, processes, files, directories, and has the ability to write files, get network parameters including host name, domain name, DNS servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, and DHCP server. The sample then communicates the collected data to a C2 server located at IP address 137[.]184[.]130[.]162. 707d22cacdbd94a3e6dc884242c0565bdf10a0be42990cd7a5497b124474889bTagstrojan Details
Antivirus
YARA RulesNo matches found. ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This sample has capability to get network parameters including host name, domain name, DNS servers, NetBIOS ID, adapter information, IP address, subnet, gateway IP, DHCP server, and additional data and communicate it to a C2 server located at IP address 137[.]184[.]130[.]162 over port 443. 74544d31cbbf003bc33e7099811f62a37110556b6c1a644393fddd0bac753730Tagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...). f5cafe99bccb9d813909876fa536cc980c45687d0f411c5f4b5346dcf6b304e4Tagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...). dedf082f523dfcb75dee0480a2d8a087e3231f89fa34fcd2b7f74866a7b6608fTagstrojan Details
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis file is a .NET DLL, which contains malicious unmanaged 64-bit Intel code. This file has the same functionality as the file "1665128935[.]8063045[.]dll" (833e9cf750...), except it does not have the capability for network communication. However, the IP address 137[.]184[.]130[.]164 is hard-coded within the sample like the other files. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. Please share your thoughts. We recently updated our anonymous Product Feedback Survey and we'd welcome your feedback. |
Source: CISA Analysis
Source Link: https://www.cisa.gov/news-events/analysis-reports/ar23-074a