
By Thorsten Rosendahl and Tiago Pereira, with contributions from Matthew Miller.
The industry has come a long way in terms of improving how we make user authentication more secure. From the most basic concept of relying on usernames and passwords for authentication to enabling multi-factor authentication (MFA) for additional security, we are now embracing a shift toward passwordless logins and/or passkeys that are designed with security in mind from the beginning.
We anticipate that passwords may disappear in a not-so-distant future, with actors likely to shift away from basic phishing or other attacks that target passwords, toward post-authentication session theft, or the weaker registration, recovery, and revocation processes.
We can broadly group the distinct types of authentication as follows:
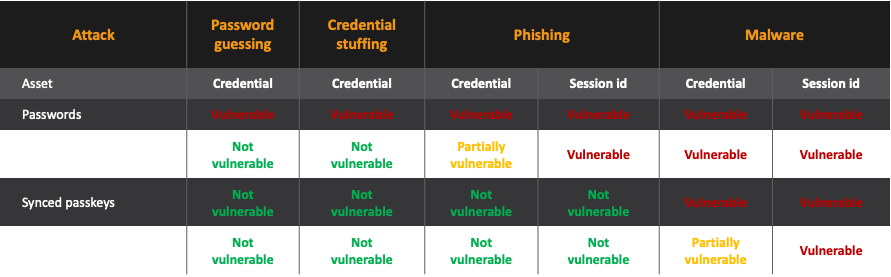
Password-based authentication is the weakest type of authentication, and it is vulnerable to several types of attacks, such as brute force, phishing and password stuffing, in which an attacker tries to use credentials that are obtained from a breach in some online service to log into other online services and applications.
Multi-factor authentication (MFA) is an authentication method whereby a user must present two or more factors to successfully pass an authentication. MFA, when passkeys are not one of the factors, protects the user against several attacks, most notably those that rely on password guessing (e.g., brute force and password spraying) and those based on credential leakage from third-party websites (e.g., password stuffing). However, it does not protect against all phishing attacks.
An attacker can redirect a user to a legitimate-looking phishing website that proxies all the information between the victim, itself, and a legitimate website. Once the victim unknowingly visits the malicious site, they are prompted to submit their credentials and accept an MFA authentication request. After this happens, the legitimate website will generate a session ID that the attacker can steal and use to access the application posing as the victim.
Device-bound passkeys are a form of passwordless authentication based on the open FIDO2 (Fast Identity Online) standard that is supported by most modern browsers and operating systems and allows users to log into websites simply clicking a button or touching a biometric reader on the device or on a mobile device. This wide support and its usability features make passkeys a viable alternative to even usernames and passwords that are combined with MFA.
In short, instead of putting the burden on the user to create and memorize unique, complex passwords for each service they use, FIDO2 credentials provide a cryptographic solution that offers stronger authentication than common MFA techniques (SMS, OTP, Push) allow. FIDO2 uses a public/private key pair, where the private key is stored on the user’s device, and the public key is registered with the online service provider.
This mechanism has several advantages over password-based and MFA authentication:
- It is phishing resistant — The browser is responsible for checking if the authenticator contains passkeys for a given URL. For example, when opening a phishing website, the browser would find that the authenticator does not have a stored credential for it, so it would not provide the user a way to login.
- It is resistant to credential stuffing – The public key is not a secret, and it is unique for each website. Even if a third-party website is breached and the public key stolen, it cannot be used by attackers to authenticate as the user.
- Private keys can be protected by hardware — The private key can be forced to be protected by a hardware module from which it cannot be exported. The private key is only used within that hardware module to create a signature and it is never exposed to a potentially compromised operating system. However rare, there have been vulnerabilities found in hardware modules that may allow attackers to steal private keys.
- It is more user-friendly - Users no longer must remember, manage, or write passwords. Instead, the user only needs a couple of clicks to quickly log in via a ceremony handled by the browser.
Although FIDO2 has many advantages over other means of authentication, it does not change how the application session mechanism works. Therefore, on a compromised device, an attacker can still steal the session ID post-authentication and use it to access the application, posing as the user.
Synced passkeys, also known as FIDO2 multi-device credentials, are like regular FIDO2 credentials, but they can be copied between user devices, allowing a user to only register once with a relying party and synchronize their key across all his devices. This is a significant step toward the adoption of passwordless authentication, as it minimizes the risk that the user loses access to their private keys and avoids the trouble of having to register and manage multiple devices and keys.
However, this increase in usability comes at a cost in security. The need to copy private keys to the cloud and to other devices means that they can be compromised if an attacker is able to register a new device posing as the victim or if the passkey implementation allows them to be stolen from the operating system memory or disk.
How phishing-resistant authentication could change the threat landscape
Although it will likely take several years for passwordless authentication to become widely adopted, and it is likely that passwords will be around for a long time, some of the most popular and most targeted applications may adopt it in the near future. Removing passwords from even a few dozen key web applications is likely to affect the threat landscape.
Targeting registration, recovery and revocation process flaws
Authentication is only one part of a larger identity management process. As much as phishing-resistant authentication is a significant increase in web application security, there are processes that must exist to allow the user to be able to use passwordless authentication, in particular, registration, revocation and recovery. This could lead to some changes in the way attackers use phishing to obtain access to target applications. For example:
Phishing for cloud providers – What happens when you lose access to all your devices at the same time? The answer is usually that the cloud provider allows a user to log in with a less secure method, which may be phishable. Because this fallback system exists, attackers will try to phish the users, leading them to provide all the details needed to recover from a scenario in which all device access was lost.
Phishing for password managers – As password managers start to store passkeys, they may become a larger target for phishing attacks, as they are the “master key” to obtaining phishing-resistant credentials. Like cloud providers, most password managers allow users to use MFA when installing it on a new device. This means that, ironically, in a passwordless future, it is possible that password managers will become a bigger target for phishing attacks.
Phishing for email providers – It is common to send “magic links” to a registered user email address that, when clicked, takes the user to a page where his password can be reset. The same system can be used for passkey re-registration. This could make email providers an even more common target for phishing attacks, as they become a way to bypass the phishing-resistant authentication on other targeted applications.
Targeting sessions, not authentications
Phishing-resistant authentication eliminates attacks that steal login credentials, leaving post-auth session IDs as the most valuable assets. Consequently, it is possible that attacks targeting session IDs will increase in popularity. These are some examples of ways the session could be attacked that could see an increase as passwords start to disappear:
Attacks based on bookmarklets – Bookmarklets are a feature of web browsers that allow JavaScript code to be saved as a bookmark. When the user clicks on the bookmark, the code is executed in the context of the open browser page. One example of this is a recent attack where bookmarklets were used to steal the Discord token from users of several Discord communities focused on cryptocurrency.
Attacks involving the clipboard – Tricking a user into executing malicious JavaScript or system commands by copy-pasting them from a website into the address bar, browser developer tools, or even the terminal can be used to steal session IDs from the browser or from the file system. This can happen as a result of social engineering, such as when users are following a tutorial that involves copy-paste code from a webpage. As a way to make these attacks more effective, pastejacking can be used to replace apparently innocuous code copied from a webpage with malicious code, tricking even more advanced users.
Browser-based malware changes – As session IDs increase in value, malware focused on the browser (for example, intercepting browser communications, injecting code into web pages or instrumenting hidden browser windows) may be subject to changes that assist new attacks and malicious business models. For example, adding features such as keeping sessions alive once they are stolen or proxying attacker HTTP requests within the context of the victim browser sessions.
Although not a threat landscape change, as session theft, becomes a major vector of compromise, it is possible that session security is increased, leading to bigger changes. Several session protection techniques that exist today may become more widely adopted, including regenerating the session ID frequently during an established session and reducing the session timeout or denying access to the session id from JavaScript. Much like what has happened to authentication, new standards could be developed that focus on the protection of web sessions.
Cybercrime business models adapt to the change
Many of the passwords that attackers are currently harvesting will be rendered obsolete with the adoption of passwordless authentication. This may cause changes both in malware and in cybercriminal’s business models built around selling access to compromised accounts:
Malware-based attacks may increase – Criminals are not likely to give up entirely because phishing has become harder or impossible. The groups that are currently dedicated to phishing could be forced to take the next step and focus on malware-based attacks. This shift could result in an increase in malware-based attacks, using the same distribution channels that phishing groups are used to (e.g., email or instant messaging).
Business models around selling compromised accounts may change – To take advantage of the stolen session IDs, attackers will have to act quickly while the session is active. As selling or taking advantage of valid session IDs becomes harder, attackers will adapt. We are already seeing signs of this adaptation. For example:
- Phishing kits commonly make use of telegram bots to allow attackers to react faster when a new session ID is stolen.
- The dark web Genesis market, which is back up again after being taken down by law enforcement a few months ago, specializes in selling “bots” which is the terminology the market owners used to call a package with a victim’s browser credentials’ cookies and fingerprints. To make this data easier to use, the market provides a specialized browser and Chrome extension to its customers, so they load the purchased “bot” data and easily use the authenticated sessions of each purchased bot. The user has the possibility of using the victim’s browser as a proxy, to make the abuse even harder to detect.
As criminals focus on sessions and these become increasingly more secure, the business models can adapt even further. For example, instead of selling stolen sessions, attackers could sell access to automated malicious actions to be triggered each time a session is compromised to the highest bidder, like high-frequency trading used in stock markets.
Web application vulnerability value increase – Web applications, just like any other software, can contain vulnerabilities introduced during development. Many of these allow an attacker to steal valid sessions or perform malicious actions directly without targeting the session. It would not be surprising if, with the unavailability of phishing as an attack vector, web app vulnerabilities became more commonly traded on underground forums and saw their value increase.
While the exact predictions in this post may or may not ever take place, passwordless authentication is gaining traction and it is certainly in the future of web authentication. Inevitably it will bring changes to attack techniques for which we should prepare sooner rather than later.
Source: Cisco Talos
Source Link: https://blog.talosintelligence.com/what-might-authentication-attacks-look-like-in-a-phishing-resistant-future/