
New research by Recorded Futures Insikt Group examines North Koreas cyber strategy. Despite the ever-increasing number of cyberattacks publicly attributed to North Korea, the regime does not publish an official cyber-strategy doctrine. North Korea's cyber strategy is focused on aggressive information collection and financial theft operations to support its goals of maintaining the Kim family dynasty and unifying the Korean peninsula under its leadership. The regime conducts information collection to gain insights into the thinking of its adversaries and to access technology that can provide an advantage during times of conflict. Financial theft is used to fund the regime's activities, including its nuclear and missile programs. Despite its centralized leadership system, North Korea creatively targets a wide range of industries across different countries.
A quantitative analysis of 273 cyberattacks attributed to North Korean state-sponsored threat actors reveals that the regime primarily engages in cyber espionage and financial theft activities. While it has the capability to conduct disruptive or destructive cyberattacks, it rarely does so. South Korea and the United States are the most common targets, but North Korean threat actors have a global reach, targeting entities in at least 29 countries. Cryptocurrency heists are on the rise, but espionage remains the primary goal of North Korean cyberattacks.
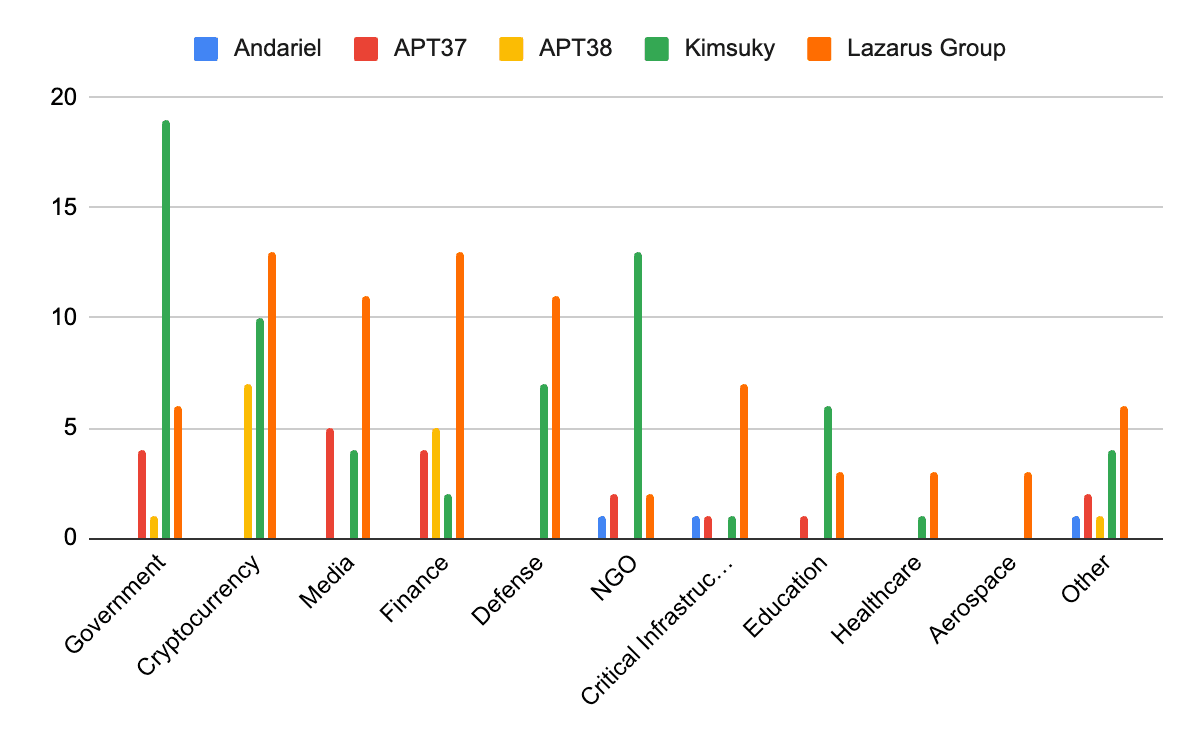 Breakdown of industry verticals of victims grouped by North Korean state-sponsored threat actors
Breakdown of industry verticals of victims grouped by North Korean state-sponsored threat actors
North Korea's cyber strategy is part of its larger asymmetric strategy to achieve the perpetuation of the regime and the unification of the Korean peninsula. The regime has invested in STEM education and nurtures talented individuals in computer science. Students are sent to domestic and international institutions for further education and exposure to technology not easily accessible in North Korea due to sanctions. The regime also deploys IT workers for online services and freelance platforms, which may overlap with cyber operators.
The report presents a comprehensive analysis of cyberattacks attributed to North Korean state-sponsored threat actors. It examines the threat actor groups involved, their targets, purpose of the attacks, and geographical distribution. Kimsuky is the most common threat group, followed by Lazarus Group and APT37. The data set covers attacks from 2009 to 2023, with a significant increase in the number of reported cyberattacks from 2016 onwards. Kimsuky's activity has seen a dramatic increase in recent years.
Overall, North Korea's cyber strategy is focused on information collection, financial theft, and espionage. The regime has developed a considerable cyber capability and targets various industries globally. However, destructive cyberattacks are rare, and the regime continues to invest in training cyber operators to further its strategic goals.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/north-koreas-cyber-strategy