
Editors Note: This is an excerpt of a full report. To read the entire analysis with endnotes, click here to download the report as a PDF.
Executive Summary
As organizations continue virtualizing their critical infrastructure and business systems, threat actors deploying ransomware have responded in kind. Between 2021 and 2022 we observed an approximately 3-fold increase in ransomware targeting ESXi, with offerings available from many groups including ALPHV, LockBit, and BlackBasta. We identified and described detection strategies for multiple TTPs that are often seen prior to the dropping of the ransomware payload in order to create detections and mitigations that are based on real-world, threat-actor use of these tools. In addition to providing tool-specific detections such as YARA and Sigma rules, we also identified detections for common enumeration, exploitation, and persistence techniques. The detections and mitigations provided can be used not only for the tools assessed below but also for custom (threat actor-specific) tools that are outside the scope of this report. Organizations looking to threat hunt, detect, and mitigate pre-ransomware TTPs for ESXi systems should use the detections provided as a starting point to develop detections specific to their environment and as part of a layered security approach. The infancy of defensive products such as endpoint detection and response (EDR) or antivirus software (AV) currently available for ESXi, combined with organizations increased reliance on virtualization, creates an attractive target for threat actors and can potentially lead to operational downtime and reputational damage to an organization.
Key Takeaways
- Ransomware targeting ESXi will continue to be a threat to organizations, putting them at risk of operational downtime, competitive disadvantage, and damage to their brand.
- Organizations should continue to deploy virtualized infrastructure, but it is critical to implement security best practices and similar precautions as used in existing infrastructure.
- The malicious tools targeting ESXi primarily abuse native commands to perform their actions, making them difficult to differentiate from normal system administrator activity.
- Openly available tools and device search engines will continue to be used by threat actors targeting ESXi, in addition to custom tooling.
- The immaturity of antivirus and EDR solutions that cover ESXi, coupled with the difficulty of implementing security measures, lowers the technical barrier for threat actors deploying malware on ESXi compared with those targeting Windows.
- Exploiting vulnerabilities for initial access is a common tactic; however, many threat actors simply rely on system administrator notes, stored passwords, or keylogging specific employees to gain access to a vSphere environment.
- Defensive practices are difficult to implement due to the complex nature of hypervisors; however, implementing utilities that provide host attestation, reduce the attack surface, and minimize access to other systems on the network can greatly reduce risk for organizations.
Background
Ransomware groups continue to evolve and expand their toolsets, focusing on more specialized targets and creating more refined tooling based on opportunities to make money. VMware ESXi is the market-leading, enterprise-grade hypervisor designed for deploying and serving virtual infrastructure. ESXi-targeting ransomware will continue to present a threat to organizations that are shifting towards virtualizing the majority of their server infrastructure. The practice of securing virtualized infrastructure is complicated due to the proprietary nature of the technology and the relative infancy of defensive products designed for it. As a result of these factors, ESXi presents an exceptionally attractive target for financially motivated threat actors.
In 2020, there were very few mentions of ESXi ransomware attacks, as threat actors primarily targeted Windows-based networks due to the availability of initial access presented by the pandemic and multiple critical vulnerabilities (such as CVE-2018-13379, CVE-2019-11510, and CVE-2019-19781). As organizations responded with more effective defenses against ransomware and threat actors recognized the defensive gaps in virtualized networks, threat actors began to create ESXi-specific ransomware and techniques. In 2021, cyberattacks involving ESXi ransomware increased. During 2022, we observed a 3-fold year-over-year increase in ransomware attacks by a larger number of ransomware groups and advanced TTPs and tooling targeting virtualized infrastructure, as seen in Figure 1 below.
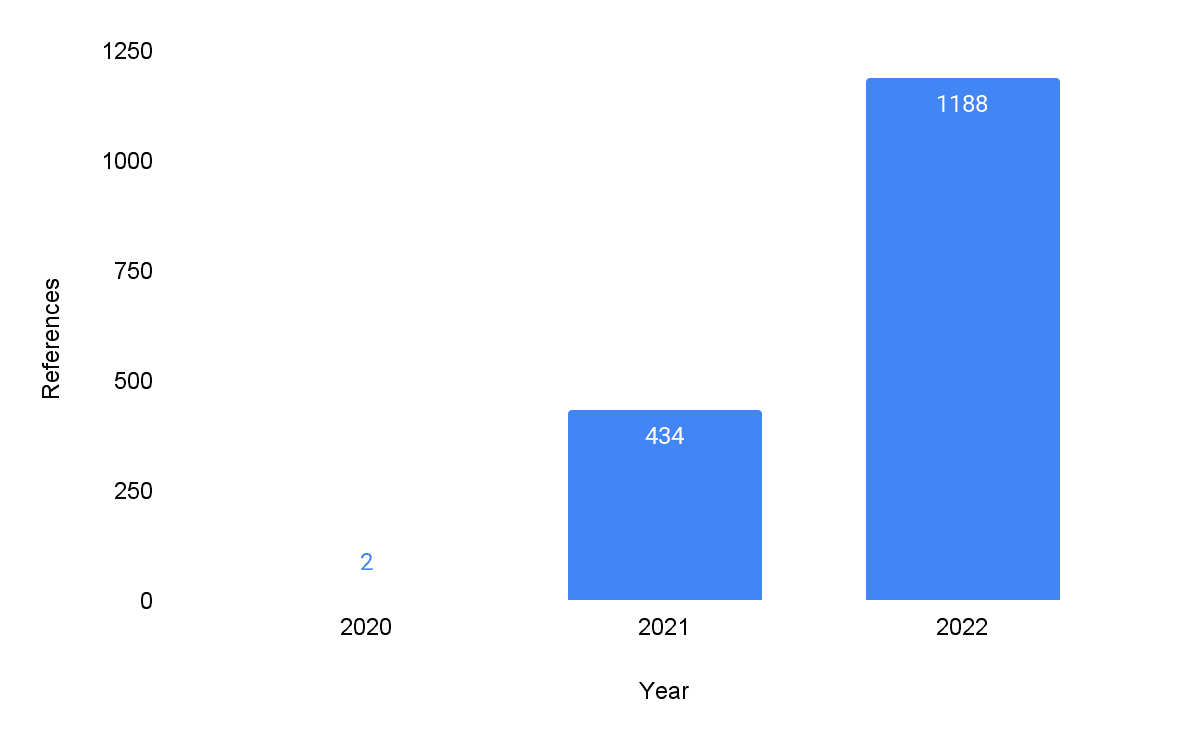 Figure 1: Ransomware attacks focused on ESXi show a 3-fold increase in a single year (Source: Recorded Future)
Figure 1: Ransomware attacks focused on ESXi show a 3-fold increase in a single year (Source: Recorded Future)
Editors Note: This is an excerpt of a full report. To read the entire analysis with endnotes, click here to download the report as a PDF.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/in-before-the-lock-esxi