Experts observed the SmokeLoader malware delivering a new Wi-Fi scanning malware strain dubbed Whiffy Recon. Secureworks Counter Threat Unit (CTU) researchers observed the Smoke Loader botnet dropping a new Wi-Fi scanning malware named Whiffy Recon. The malicious code triangulates the positions of the infected systems using nearby Wi-Fi access points as a data point for Google’s […]
The post Whiffy Recon malware triangulates the position of infected systems via Wi-Fi appeared first on Security Affairs.
Experts observed the SmokeLoader malware delivering a new Wi-Fi scanning malware strain dubbed Whiffy Recon.
Secureworks Counter Threat Unit (CTU) researchers observed the Smoke Loader botnet dropping a new Wi-Fi scanning malware named Whiffy Recon. The malicious code triangulates the positions of the infected systems using nearby Wi-Fi access points as a data point for Google’s geolocation API.
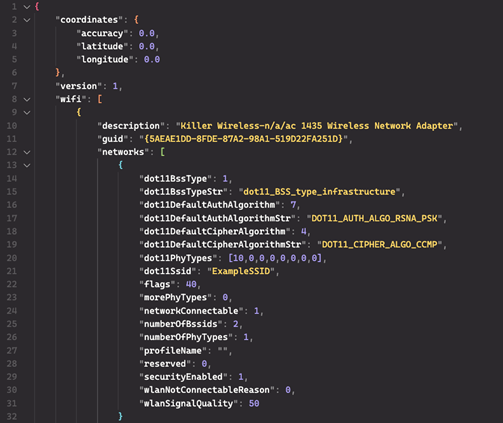
“The scan results are mapped to a JSON structure (see Figure 5) that is sent to the Google Geolocation API via an HTTPS POST request. The Google Geolocation API is a legitimate service that triangulates a system’s location using collected Wi-Fi access points and mobile network data and returns coordinates. The Whiffy Recon code includes a hard-coded URL that the threat actors use to query the API.” reads the report published by Secureworks.
“These coordinates are then mapped to a more comprehensive JSON structure that contains detailed information about each wireless access point found in the area. This data identifies the encryption methods used by the access points.”
The experts noticed that the Whiffy Recon’s main code runs as two loops. One loop registers the bot with the C2 server, and the second performs scanning for Wi-Fi access points via the Windows WLAN API. This second loop runs every 60 seconds. The malware register with a remote C2 using a randomly generated “botID” in an HTTP POST request. In turn the server reply with a success message and a secret unique identifier that is saved in a file named “%APPDATA%\Roaming\wlan\str-12.bin.”
Whiffy Recon checks for the WLAN AutoConfig service (WLANSVC) on the infected system and terminates itself if the service name doesn’t exist. The malware maintains persistence on the system by creating the wlan.lnk shortcut in the user’s Startup folder.
Smoke Loader is a tiny dropper used to install on the infected system other malware families
The researchers have yet to determine the motivation of the operators behind this malware.
“Because the Wi-Fi scanning occurs every 60 seconds and is enriched with geolocation data, it could allow the threat actors to track the compromised system. It is unclear how the threat actors use this data. Demonstrating access to geolocation information could be used to intimidate victims or pressure them to comply with demands.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Whiffy Recon)
The post Whiffy Recon malware triangulates the position of infected systems via Wi-Fi appeared first on Security Affairs.
Source: SecurityAffairs
Source Link: https://securityaffairs.com/149854/malware/whiffy-recon-malware.html