SummaryDescriptionCISA received three files for analysis. The files included three webshells written in PHP: Hypertext Preprocessor (PHP), Active Server Pages Extended (ASPX), and .NET Dynamic-Link Library (DLL). The sample “sd.php” is highly obfuscated and uses rot13 algorithm, zlib for compression and base64 encoding for obfuscation. The “osker.aspx” webshell code was padded with junk code. The .NET DLL webshell is a .NET compiled version of osker.aspx. The samples are interactive webshells and have the ability to upload and manage files, create directories and files, and execute commands on the target machine. For more information about this compromise, see Joint Cybersecurity Advisory Threat Actors Exploit Progress Telerik Vulnerabilities in Multiple U.S. Government IIS Servers Download the PDF version of this report: For a downloadable copy of IOCs, see below or the JSON file. Submitted Files (3)6ce087b904af8a01aae73ac77d81822ad41799f89a5d301dce45191c897012aa (osker.aspx) b63c95300c8e36b5e6d3393da12931683796f88fd4601ba8364658b4d12ac05b (App_Web_jl37rjxu.dll) ea98368f6ecb5281654a6a9e4c649ef9b53860f1ee32340145b61e0e42e1072a (sd.php) Findingsea98368f6ecb5281654a6a9e4c649ef9b53860f1ee32340145b61e0e42e1072aTagsobfuscatedtrojanuploaderwebshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. DescriptionThis sample is an obfuscated PHP interactive webshell. This webshell is encoded and obfuscated using rot13, gzinflate and base64 as seen in the following code: “eval(str_rot13(gzinflate(str_rot13(base64_decode(($sym))))));” The obfuscated code is a string and is stored in the $sym variable from where it is read and decoded upon execution (Figure 1). The webshell requires the password "pass" for authentication and uses the string “$xyn='tunafeesh';” as a cookie to authenticate. This webshell enumerates the local system it infects including the operating system, current user, directories, files and permissions. The webshell has the ability to create, rename, and delete files and directories. Furthermore, it has the ability to upload additional files to the affected webserver, run in Safe Mode and execute commands via cmd.exe (Figure 2). The webshell provides a Graphical User Interface (GUI) to the operator to perform these operations on the infected machine. ---Notable Strings Begin--- Screenshots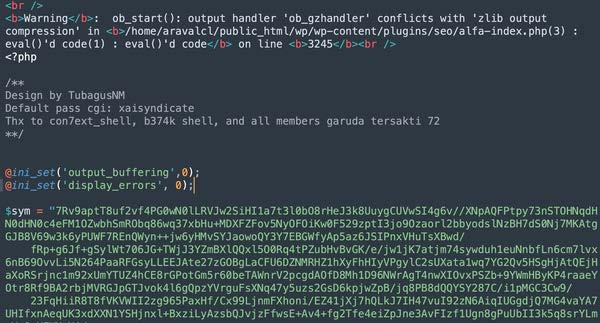 Figure 1. - $sym variable with obfuscated code.  Figure 2. - sd.php webshell interface. Threat Actor (TA) would have access to this interface remotely to conduct various actions like upload additional files, create directories and files, run commands and more. 6ce087b904af8a01aae73ac77d81822ad41799f89a5d301dce45191c897012aaTagsbackdoor trojan webshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis sample is an ASP .NET webshell. The webshell code was padded with junk code for detection evasion. The beginning of the webshell code can be seen in Figure 3. It is possible to access the webshell interactively via browser to view the GUI as seen in Figure 4. This webshell has the ability to enumerate drive name and type, software, operating system versions, processes, and users, and has ability to copy, create and delete files, directories and databases. Furthermore, this webshell is able to upload, download, run and execute commands using cmd.exe and sqlcmd.exe. This webshell has the ability to interact with and manipulate SQL databases. Furthermore, this webshell uses Windows Management Instrumentation (WMI) Management Objects to query processes, users and network domains. It is also able to encode and decode data using base64. ---Notable Strings Begin--- Screenshots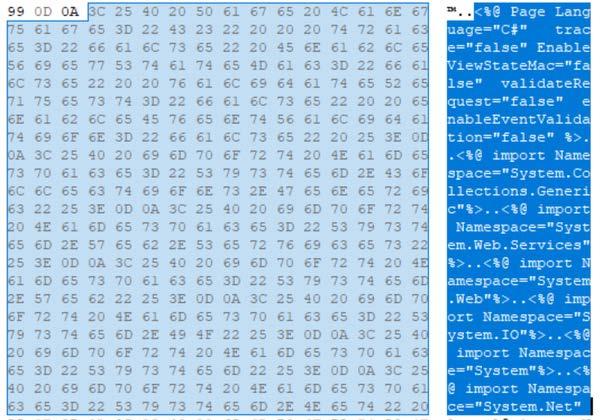 Figure 3. - Beginning of osker.aspx webshell code. 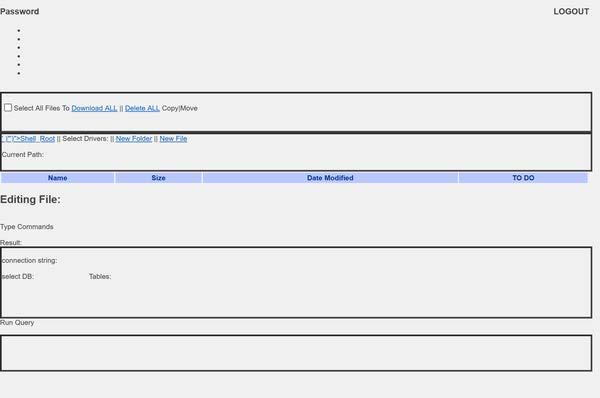 Figure 4. - Web interface for osker.aspx webshell. The webshell interface password is “321”. b63c95300c8e36b5e6d3393da12931683796f88fd4601ba8364658b4d12ac05bTagsbackdoortrojanwebshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis is a 32-bit .NET Dynamic-Link Library (DLL) file. This sample is a ASP .NET webshell and is related to the osker.aspx file. These webshells may affect Microsoft Exchange Servers and IIS services exploited by the ProxyLogon vulnerability. This sample is a .NET DLL file that is created by the ASP.NET Runtime when ASPX script is seen for the first time on the system. The capabilities and functions are identical to the osker.aspx file. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
https://www.cisa.gov/news-events/analysis-reports/ar23-166a
SummaryDescriptionCISA received three files for analysis. The files included three webshells written in PHP: Hypertext Preprocessor (PHP), Active Server Pages Extended (ASPX), and .NET Dynamic-Link Library (DLL). The sample “sd.php” is highly obfuscated and uses rot13 algorithm, zlib for compression and base64 encoding for obfuscation. The “osker.aspx” webshell code was padded with junk code. The .NET DLL webshell is a .NET compiled version of osker.aspx. The samples are interactive webshells and have the ability to upload and manage files, create directories and files, and execute commands on the target machine. For more information about this compromise, see Joint Cybersecurity Advisory Threat Actors Exploit Progress Telerik Vulnerabilities in Multiple U.S. Government IIS Servers Download the PDF version of this report: For a downloadable copy of IOCs, see below or the JSON file. Submitted Files (3)6ce087b904af8a01aae73ac77d81822ad41799f89a5d301dce45191c897012aa (osker.aspx) b63c95300c8e36b5e6d3393da12931683796f88fd4601ba8364658b4d12ac05b (App_Web_jl37rjxu.dll) ea98368f6ecb5281654a6a9e4c649ef9b53860f1ee32340145b61e0e42e1072a (sd.php) Findingsea98368f6ecb5281654a6a9e4c649ef9b53860f1ee32340145b61e0e42e1072aTagsobfuscatedtrojanuploaderwebshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. DescriptionThis sample is an obfuscated PHP interactive webshell. This webshell is encoded and obfuscated using rot13, gzinflate and base64 as seen in the following code: “eval(str_rot13(gzinflate(str_rot13(base64_decode(($sym))))));” The obfuscated code is a string and is stored in the $sym variable from where it is read and decoded upon execution (Figure 1). The webshell requires the password "pass" for authentication and uses the string “$xyn='tunafeesh';” as a cookie to authenticate. This webshell enumerates the local system it infects including the operating system, current user, directories, files and permissions. The webshell has the ability to create, rename, and delete files and directories. Furthermore, it has the ability to upload additional files to the affected webserver, run in Safe Mode and execute commands via cmd.exe (Figure 2). The webshell provides a Graphical User Interface (GUI) to the operator to perform these operations on the infected machine. ---Notable Strings Begin--- Screenshots Figure 1. - $sym variable with obfuscated code.  Figure 2. - sd.php webshell interface. Threat Actor (TA) would have access to this interface remotely to conduct various actions like upload additional files, create directories and files, run commands and more. 6ce087b904af8a01aae73ac77d81822ad41799f89a5d301dce45191c897012aaTagsbackdoor trojan webshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis sample is an ASP .NET webshell. The webshell code was padded with junk code for detection evasion. The beginning of the webshell code can be seen in Figure 3. It is possible to access the webshell interactively via browser to view the GUI as seen in Figure 4. This webshell has the ability to enumerate drive name and type, software, operating system versions, processes, and users, and has ability to copy, create and delete files, directories and databases. Furthermore, this webshell is able to upload, download, run and execute commands using cmd.exe and sqlcmd.exe. This webshell has the ability to interact with and manipulate SQL databases. Furthermore, this webshell uses Windows Management Instrumentation (WMI) Management Objects to query processes, users and network domains. It is also able to encode and decode data using base64. ---Notable Strings Begin--- Screenshots Figure 3. - Beginning of osker.aspx webshell code.  Figure 4. - Web interface for osker.aspx webshell. The webshell interface password is “321”. b63c95300c8e36b5e6d3393da12931683796f88fd4601ba8364658b4d12ac05bTagsbackdoortrojanwebshell Details-->
Antivirus
YARA Rules
ssdeep MatchesNo matches found. Relationships
DescriptionThis is a 32-bit .NET Dynamic-Link Library (DLL) file. This sample is a ASP .NET webshell and is related to the osker.aspx file. These webshells may affect Microsoft Exchange Servers and IIS services exploited by the ProxyLogon vulnerability. This sample is a .NET DLL file that is created by the ASP.NET Runtime when ASPX script is seen for the first time on the system. The capabilities and functions are identical to the osker.aspx file. Relationship Summary
RecommendationsCISA recommends that users and administrators consider using the following best practices to strengthen the security posture of their organization's systems. Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
Additional information on malware incident prevention and handling can be found in National Institute of Standards and Technology (NIST) Special Publication 800-83, "Guide to Malware Incident Prevention & Handling for Desktops and Laptops". Contact Information
CISA continuously strives to improve its products and services. You can help by answering a very short series of questions about this product at the following URL: https://us-cert.cisa.gov/forms/feedback/ Document FAQWhat is a MIFR? A Malware Initial Findings Report (MIFR) is intended to provide organizations with malware analysis in a timely manner. In most instances this report will provide initial indicators for computer and network defense. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. What is a MAR? A Malware Analysis Report (MAR) is intended to provide organizations with more detailed malware analysis acquired via manual reverse engineering. To request additional analysis, please contact CISA and provide information regarding the level of desired analysis. Can I edit this document? This document is not to be edited in any way by recipients. All comments or questions related to this document should be directed to the CISA at 1-888-282-0870 or CISA Service Desk. Can I submit malware to CISA? Malware samples can be submitted via three methods:
CISA encourages you to report any suspicious activity, including cybersecurity incidents, possible malicious code, software vulnerabilities, and phishing-related scams. Reporting forms can be found on CISA's homepage at www.cisa.gov. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Source: CISA Analysis
Source Link: https://www.cisa.gov/news-events/analysis-reports/ar23-166a