Background Across the vast landscape of attackers and defenders, it’s common to see actors and teams playing both sides for fun and profit. We mostly see this within mature red teams and APT groups, so it’s noteworthy to observe this dynamic within the context of a smaller group or even individual actors. In this blog, […]
The post Adversary On The Defense: ANTIBOT.PW appeared first on InQuest.
Background
Across the vast landscape of attackers and defenders, it’s common to see actors and teams playing both sides for fun and profit. We mostly see this within mature red teams and APT groups, so it’s noteworthy to observe this dynamic within the context of a smaller group or even individual actors.
In this blog, we will cover the lifecycle of a commercial web traffic filtering service originating from a GitHub project and how it found success within phishing operations. We’ll also discuss the evolution of the tool into a commercial platform offering under new branding.
The tool in question, known as Antibot, was designed to serve as a web traffic filtering script for websites to differentiate real users from bots. Such tooling is fairly common with the current state of the internet as we know it; the plethora of existing crawlers and scraping activity occurring regularly makes such tooling a necessity to inhibit unwanted traffic. For example, Akamai documents anti-bot tools in the context of legitimate services intended to protect online services and websites from abusive bots. Many companies across industries rely on anti-bot and traffic filtering services provided by CDNs and other types of providers to ensure the integrity of their published content and prevent abusive scraping. It becomes interesting when the use of such tooling comes into play in the context of threat actor infrastructure. The primary use cases for these tools in the malicious context include anti-analysis and anti-research, some of the highest priorities for any adversary’s operational security. This type of anti-analysis provides the basis for a feature known as cloaking, which enables an adversary to evade defensive controls by providing a misleading benign response payload to content scanning services, while at the same time providing the actual malicious payload to normal users. An attacker who can successfully evade automated web content scanners can extend the life of their phishing and malware campaigns, netting additional profits with less effort over time.
Antibot
Antibot is a PHP script, intended to be run on a web server and receiving inbound web traffic, where it can be analyzed and filtered before serving payload content to a client. The analysis performed is intended to detect automated or inauthentic bot traffic; various methods can be used for this, including evaluating HTTP request headers, cookie presence, origin IP space or traffic type, and other approaches. Version 2.6 of the script is the commonly observed version in use. Antibot likely originated during 2019, when we saw that an associated domain name was registered.
An example of an installation of Antibot from 2020 is found in a Joe Sandbox report:
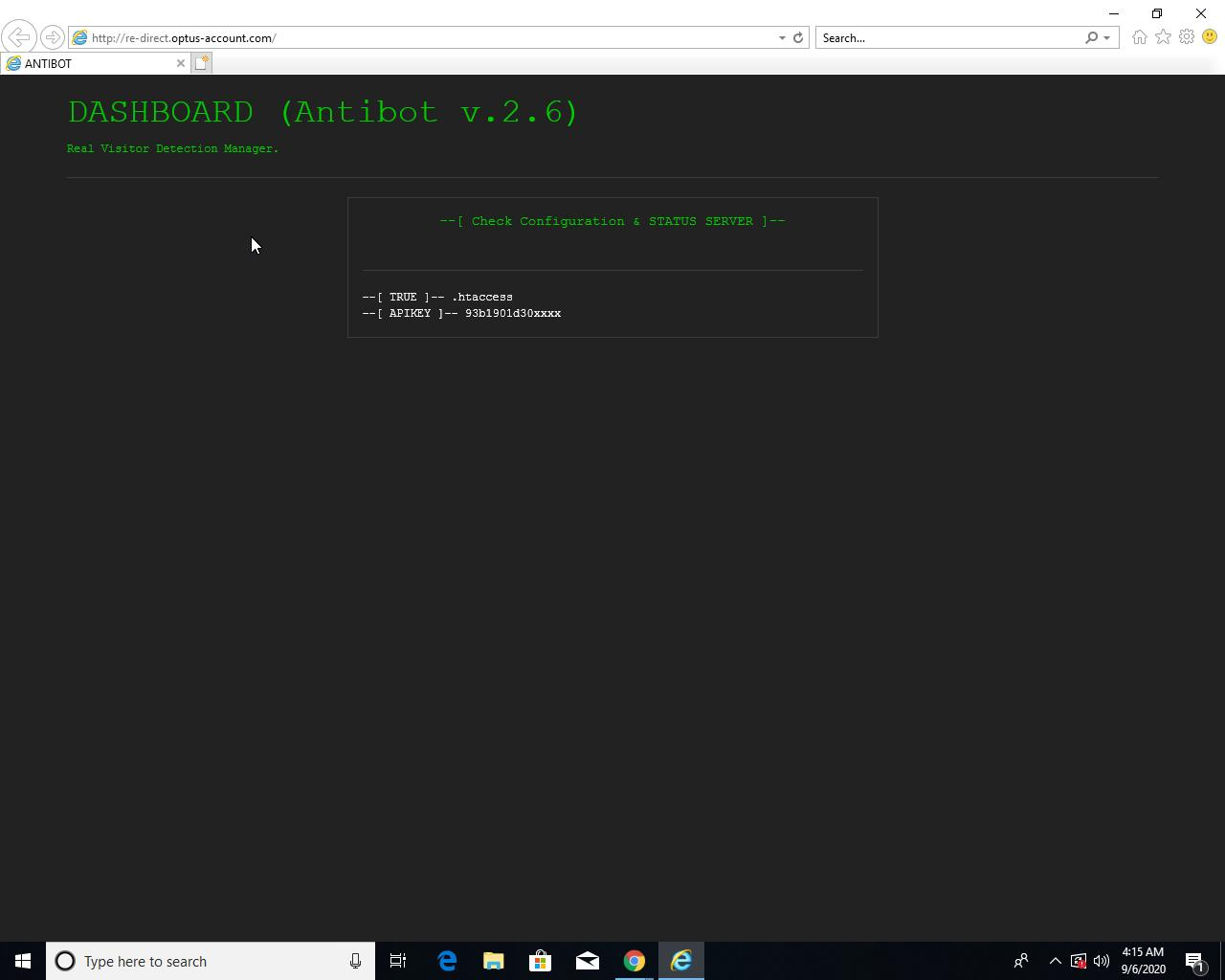
Various versions of this script may still be found installed on sites utilizing it today. For example:
- hXXps://www.wpabaseball[.]com/
- hXXps://kmbs[.]ir/index.php?option=com_content&view=article&id=165&Itemid=311&lang=fa
- hXXps://ktrlcvw[.]com/
An extended version of the control panel has also been observed, both exposed publicly and behind authentication:
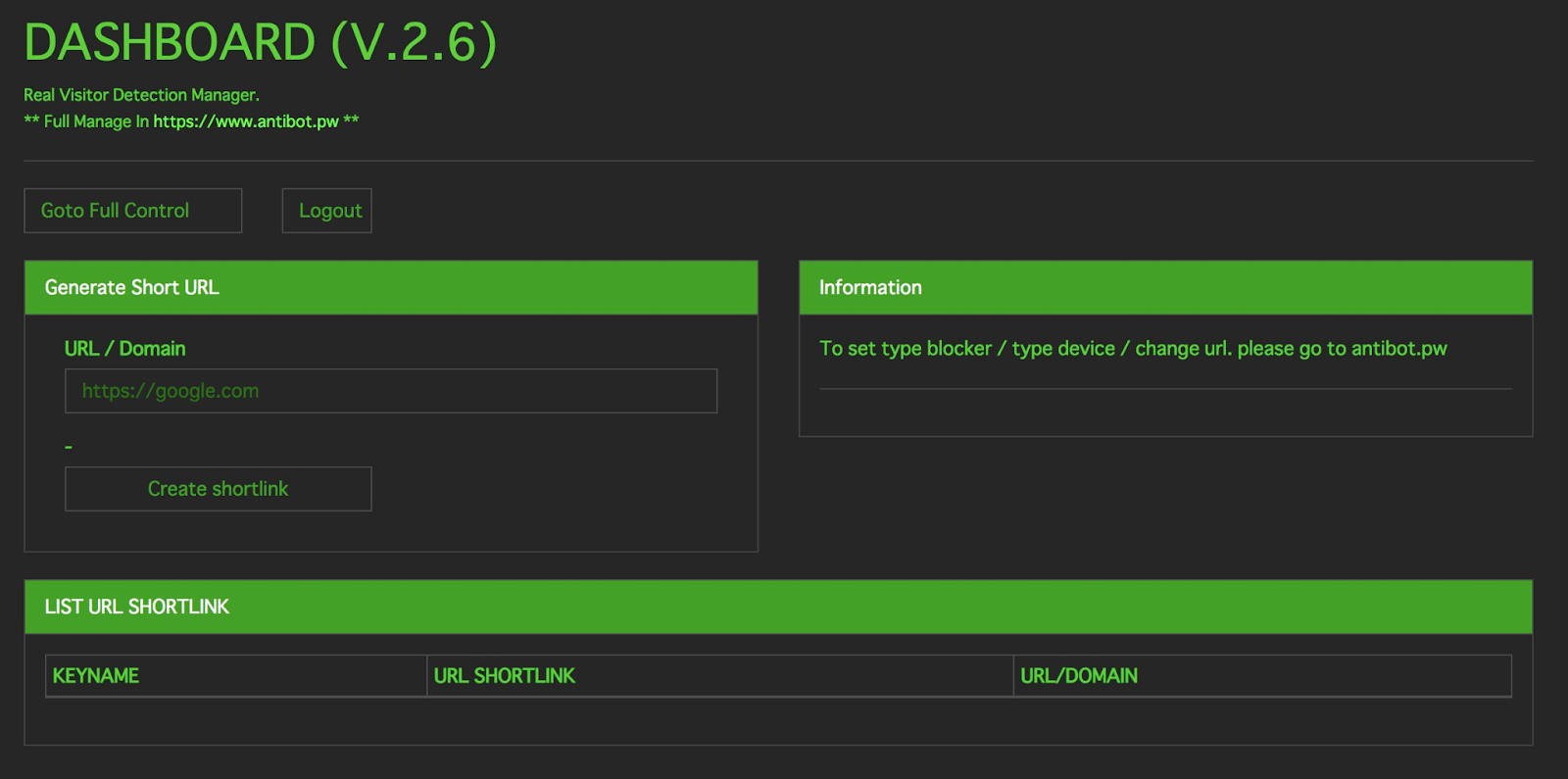
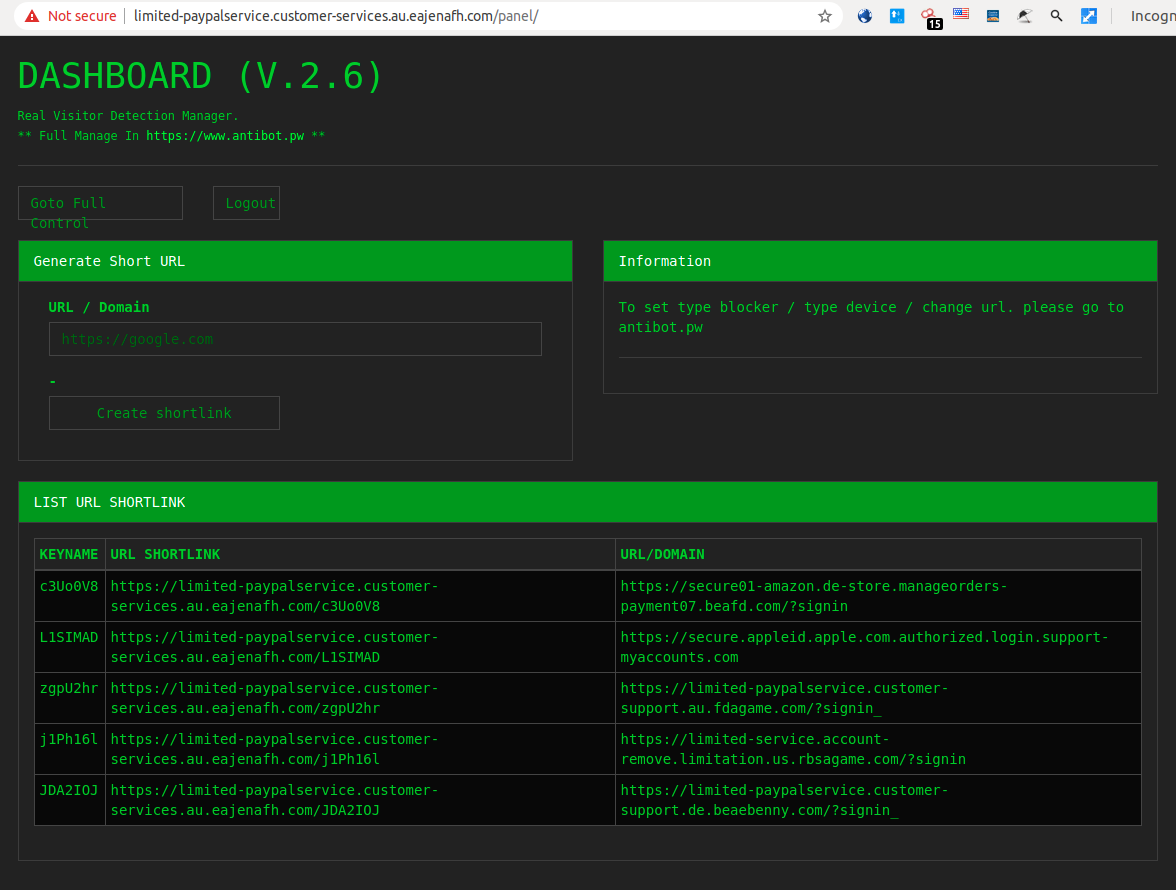
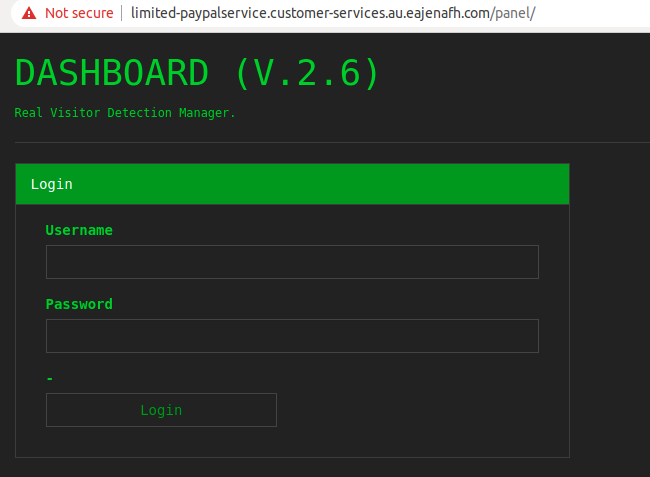
As previously mentioned, the origins of this tool appear to be a GitHub project that is currently inactive:
https://github.com/radenvodka/antibot
Installations of the control panel for the filtering software have surfaced on numerous sites and in some public reports, such as the following:
- https://twitter.com/dave_daves/status/1235528342130118657
- https://twitter.com/ninoseki/status/1250678685079728128
The reasons for the open source project going dormant likely become clear when examining the evolution of the standalone script into an online service, modernizing the offering for the underground economy.
ANTIBOT.PW and Killbot Services
Antibot originally saw life as a simple PHP script, designed for a user installation on a web server. Since this time, the GitHub project has been taken offline, and the developer has embarked on a new vision for Antibot – the ANTIBOT.PW and Killbot services are included in a set of abuse-oriented service offerings. Antibot is believed to likely be the predecessor and server-side base code component for ANTIBOT.PW. The operator of the site notes this background in the site footer:
2019-2023 © ANTIBOT.PW In 2019 antibot started with a different name (* .pw) initially we focused on shortlink service providers and within a month, we get positive feedback. in the end we developed several products and tools such as bot detection which is now in high demand, IP Geolocation and other services.
The early phases of ANTIBOT.PW were observed in 2019 as shown in this capture from urlscan.io:
A copy of an associated PHP script was posted to Pastebin during the same year:
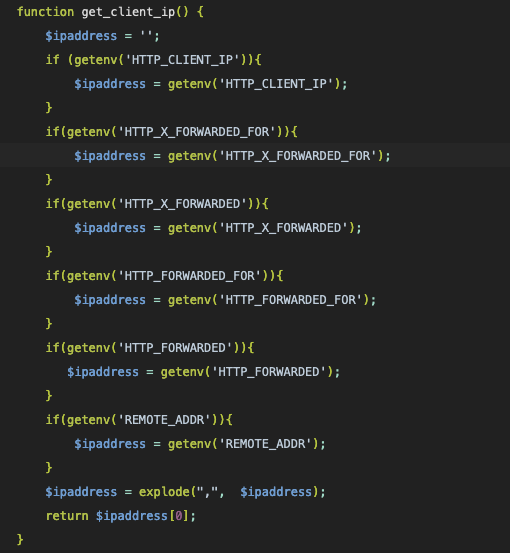
The PHP script contains an API service URL and API key for the ANTIBOT.PW service at the time. The script works in a familiar way to many other traffic filtering scripts; the client IP address and several origin IP address headers commonly used with CDNs and reverse proxies are captured by the get_client_ip() function:
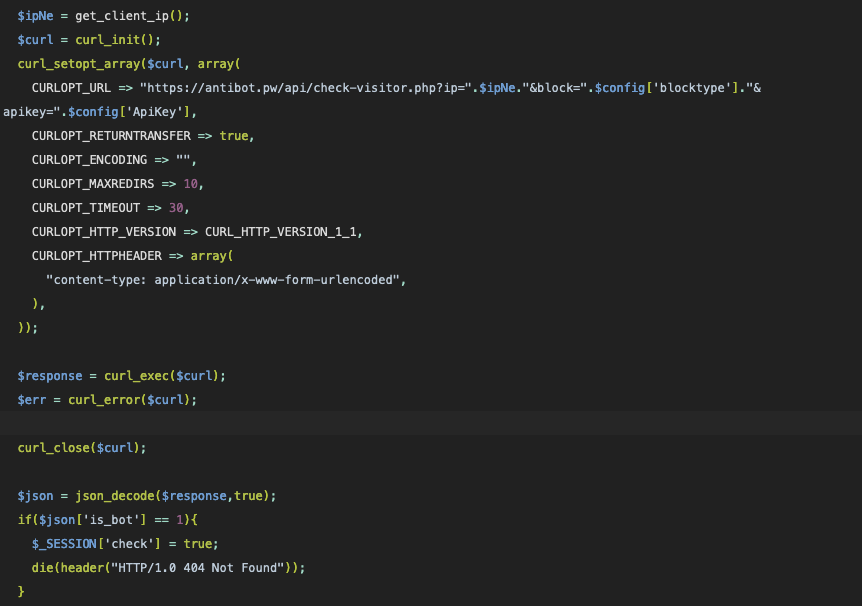
The client is checked by calling this function, resulting in a call back to the developer site, and the JSON response checks for a field called is_bot. If this field is set, then the client is filtered and is issued an HTTP 404 response:
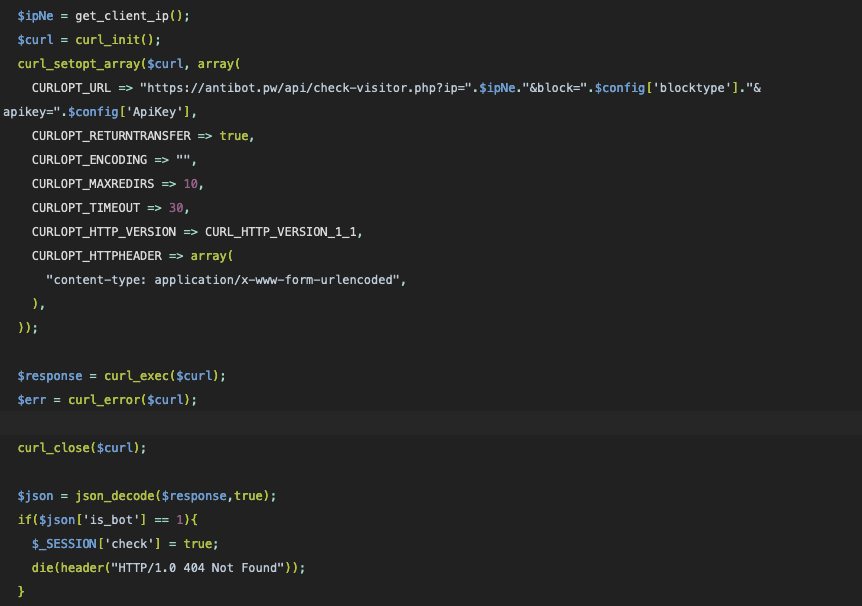
Using an alternate mode, this copy of the script also includes inline filtering content, evaluating the client’s DNS name and remote IP address against a list of blocked domains and IP wildcard expressions:
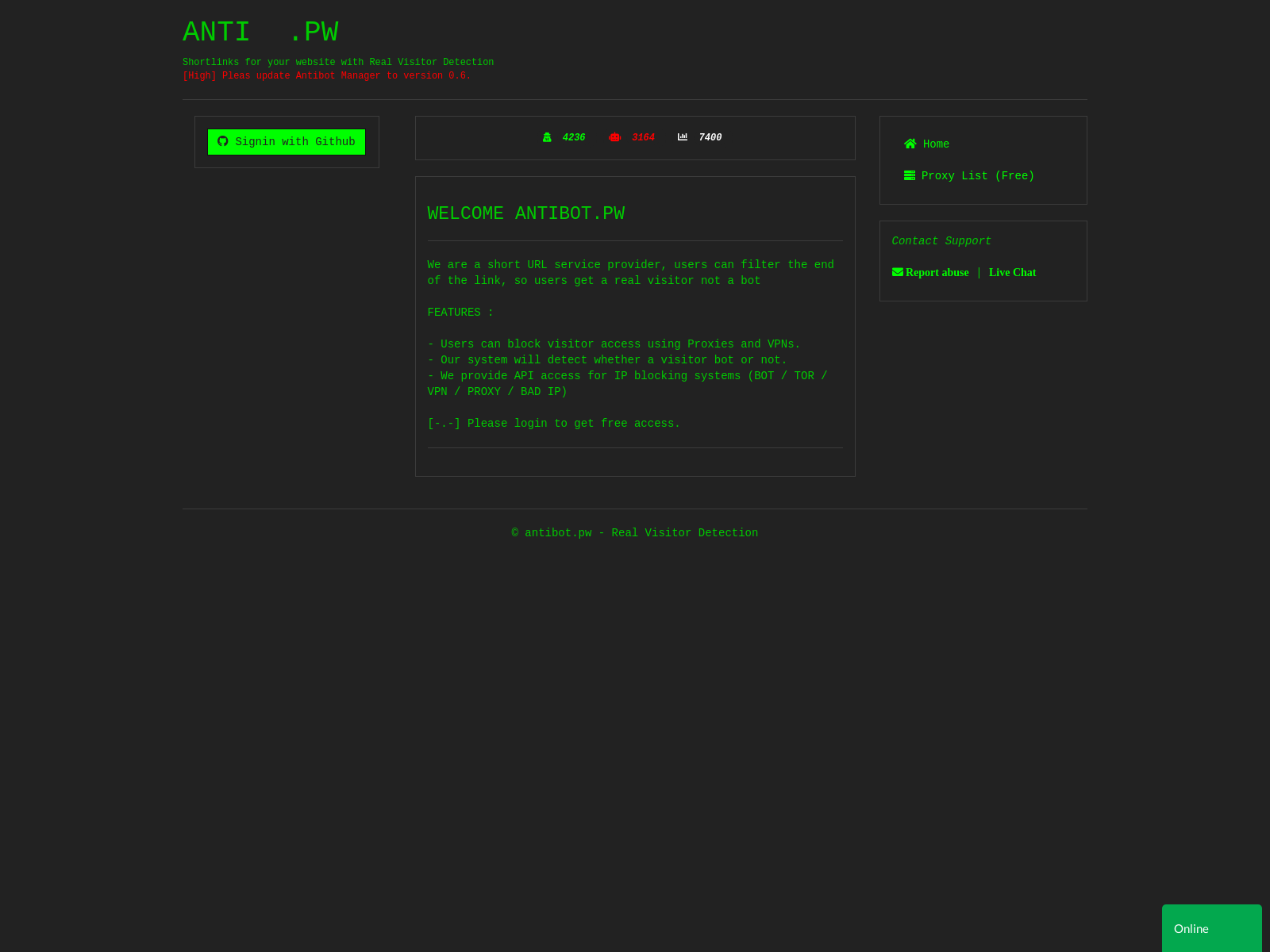
The web portal for the Antibot service lives at ANTIBOT.PW:
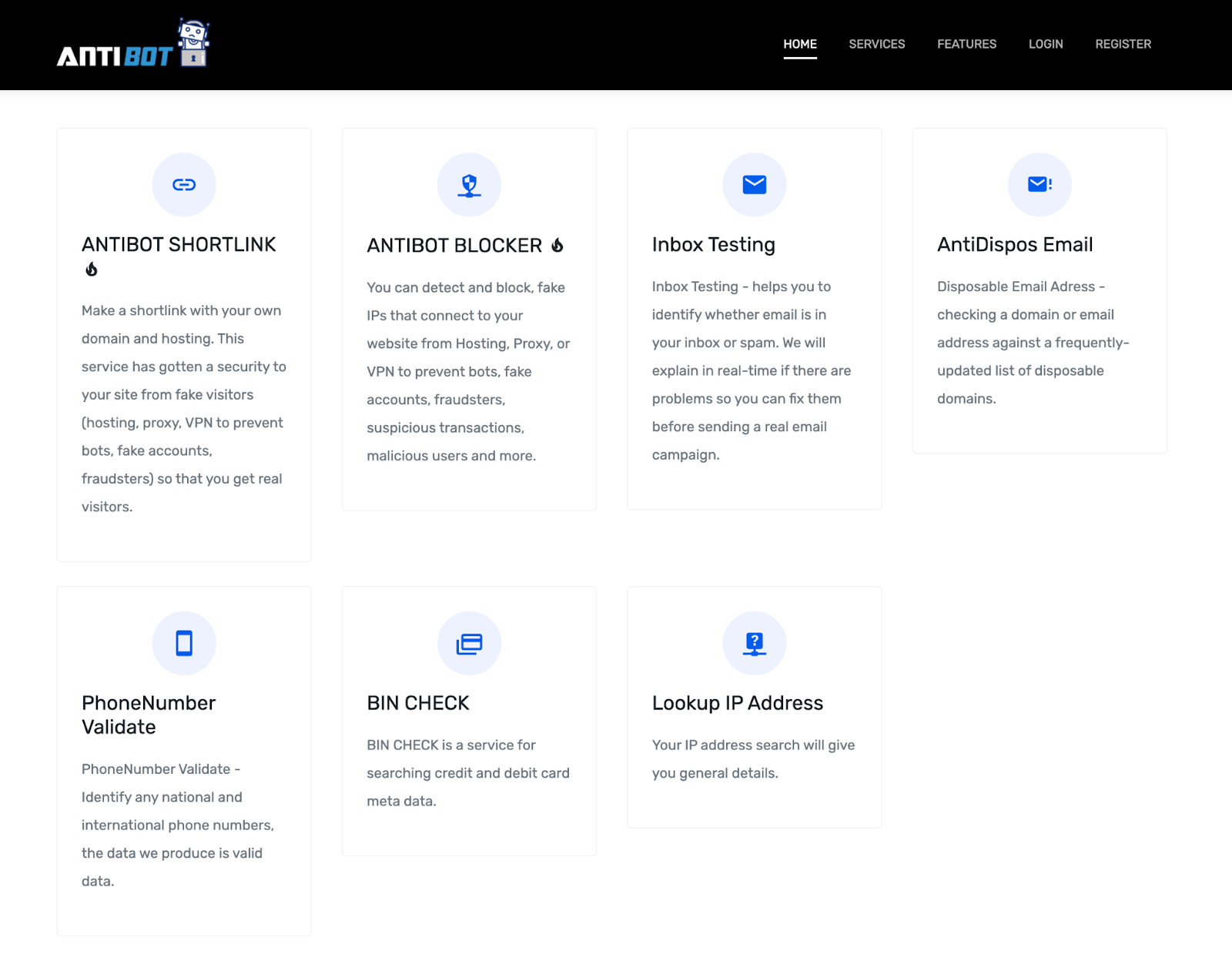
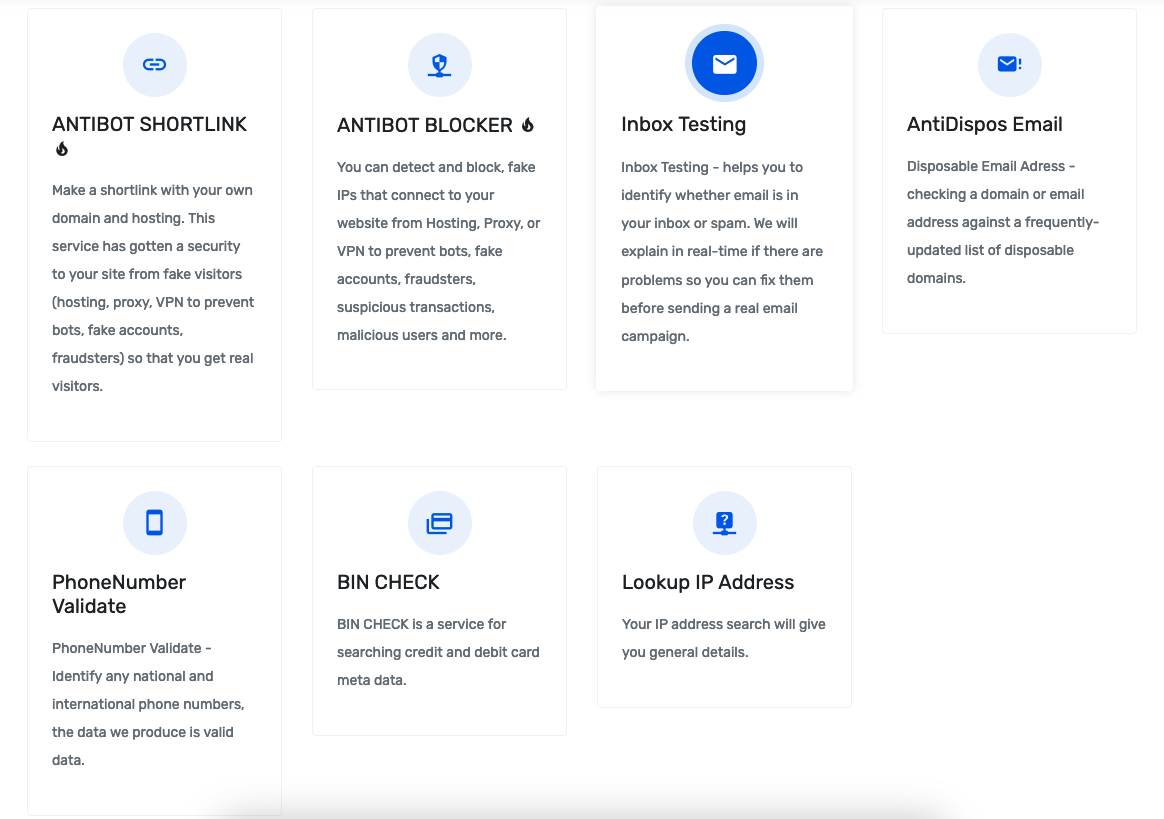
The ANTIBOT.PW service offers several features that are notably useful in the context of spamming, phishing URL misdirection, phishing submission verification, client IP address verification and carding:
- Antibot Shortlink
- Antibot Blocker
- Inbox Testing
- AntiDispos Email
- PhoneNumber Validate
- BIN CHECK
- Lookup IP Address
By 2020, other phishing services and products had been observed factoring ANTIBOT.PW in as features of their own crimeware, as noted by MalwareHunterTeam:
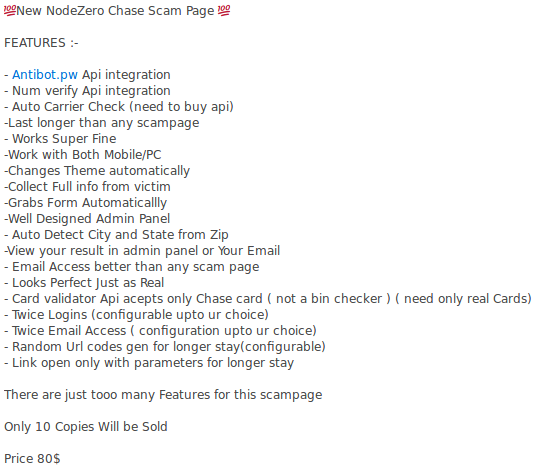
Designed as an API service for easy integration, the partnership landscape with ANTIBOT.PW is notable, particularly in the Indonesian spammer and phisher community where many of the threat actors are sure to collaborate and share a common tooling ecosystem. Data on instances of the HijaIyh phishing kit being used to target the Apple brand was shared by a researcher in 2020, noting that Antibot was bundled with the kit and effectively bypassed analysis by an online web crawler. The developer of the HijaIyh kit, another prolific phishing-as-a-service kit from the Indonesian phisher community, listed ANTIBOT.PW as a partner in the project homepage, hijaiyh[.]jp. An analysis of a Chase bank phishing campaign was shared by researchers at Sucuri in 2021, showing a similar bundling of Antibot components in the backend kit.

Killbot
By 2020, the operator of ANTIBOT.PW started to establish a new service called Killbot. Domain registrations were noted in April (KILLBOT.ORG) and July (KILLBOT.PW). Killbot attempts to take a leg up in terms of legitimate appearance, providing a more professional site designed to attract clients, while at the same time offering a similar set of services to that of ANTIBOT.PW. An unassuming user seeking website security solutions may even believe that the service is a legitimate offering, operated by a reputable company. This would of course not be the case.

The login page dialog shows the same structural similarity to ANTIBOT.PW:
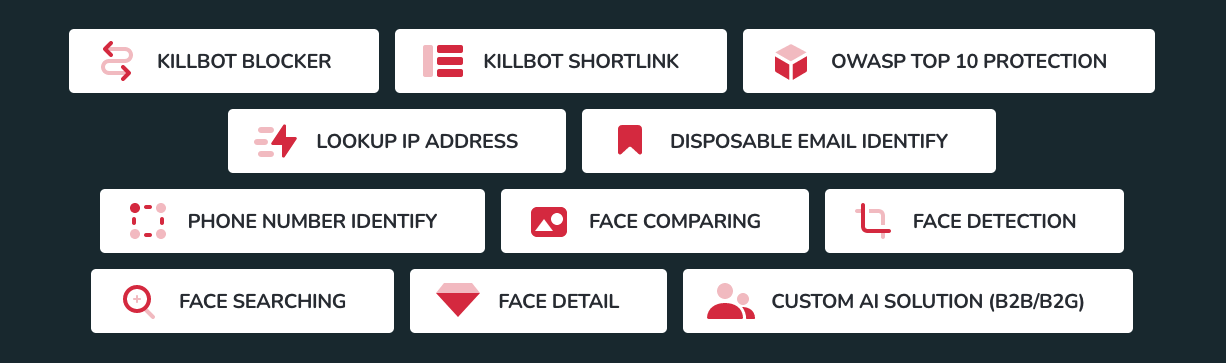
Comparing advertised features of ANTIBOT.PW and Killbot services shows similarities, with the later addition of advertising facial detail comparisons. The name Antibot Blocker is updated to Killbot Blocker, Antibot Shortlink to Killbot Shortlink, and a number of other services also remain:
- Killbot Blocker
- Killbot Shortlink
- OWASP Top 10 Protection
- Lookup IP address
- Disposable Email Identify
- Phone Number Identify
- Face Comparing
- Face Detection
- Face Searching
- Face Detail
- Custom AI Solution (B2B/B2G)
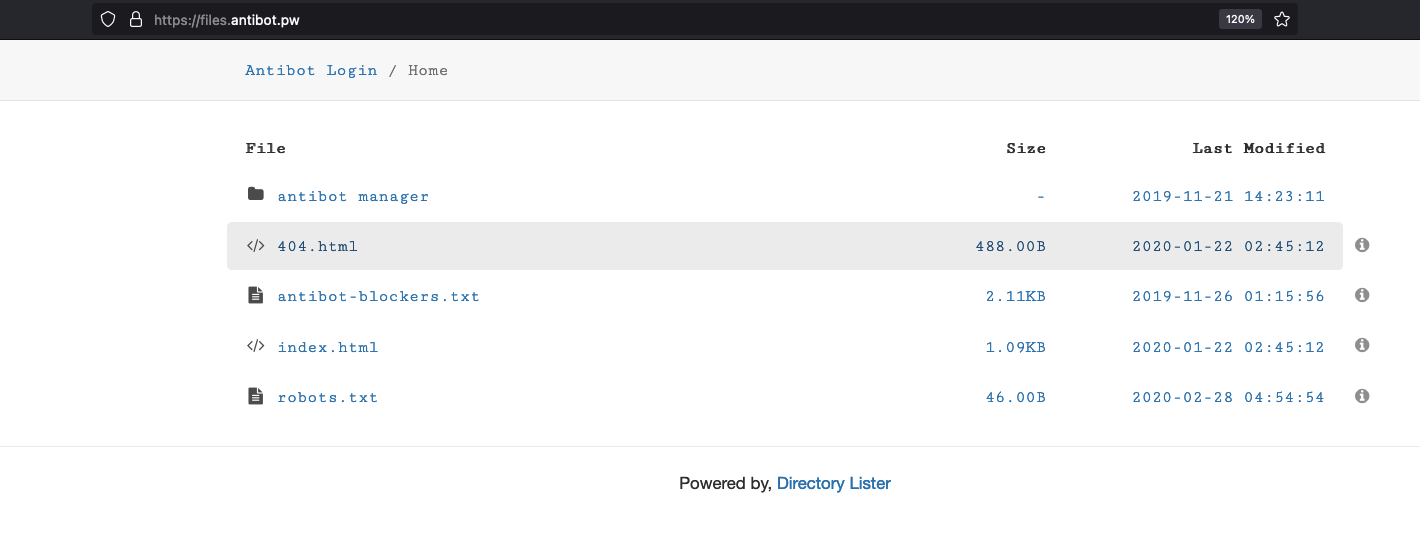
InQuest also notes direct relations in how the older ANTIBOT.PW and newer Killbot services operate. ANTIBOT.PW exposes a file repository for clients at files.antibot[.]pw:
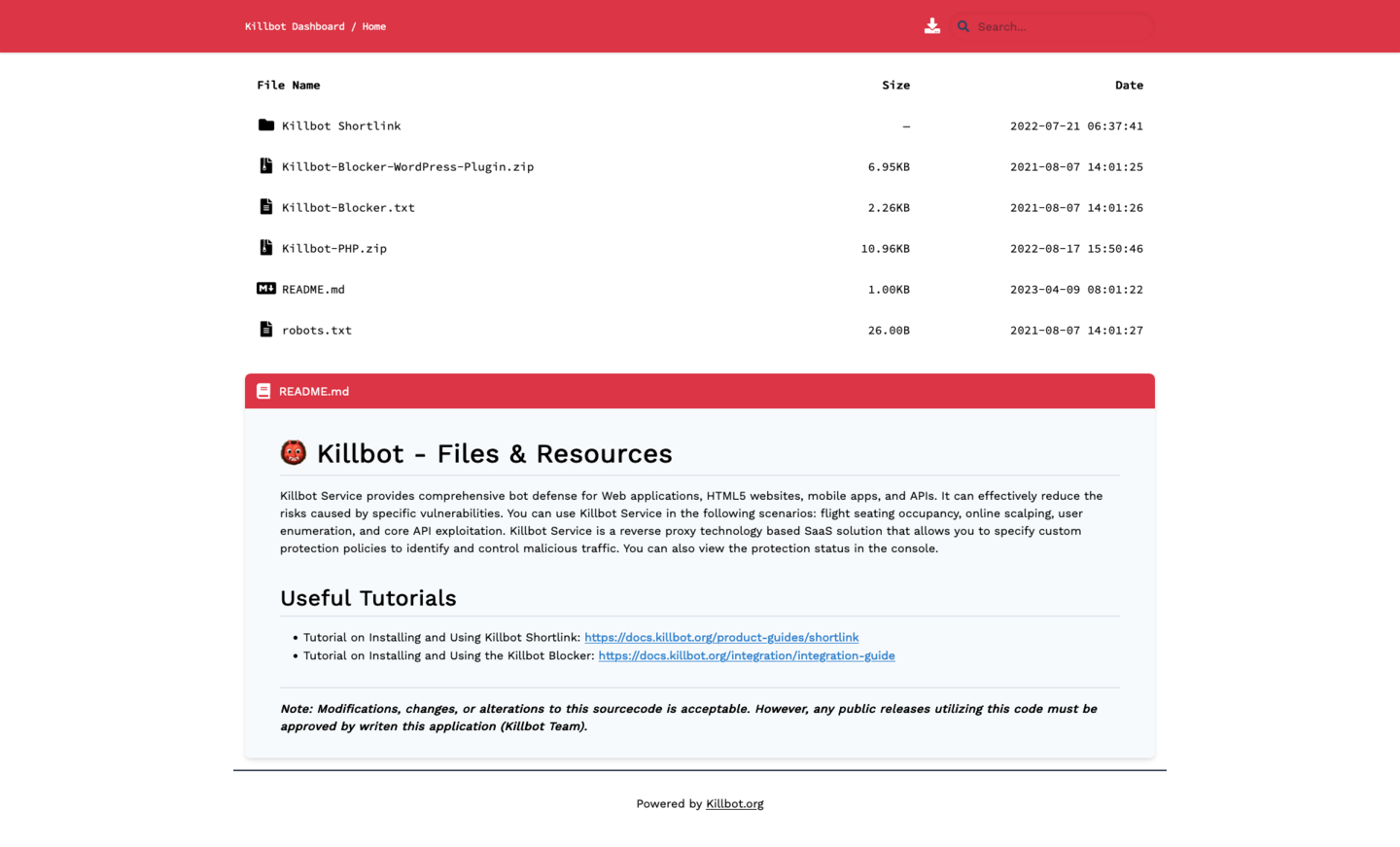
A similar file repository is hosted for Killbot at files.killbot[.]org:
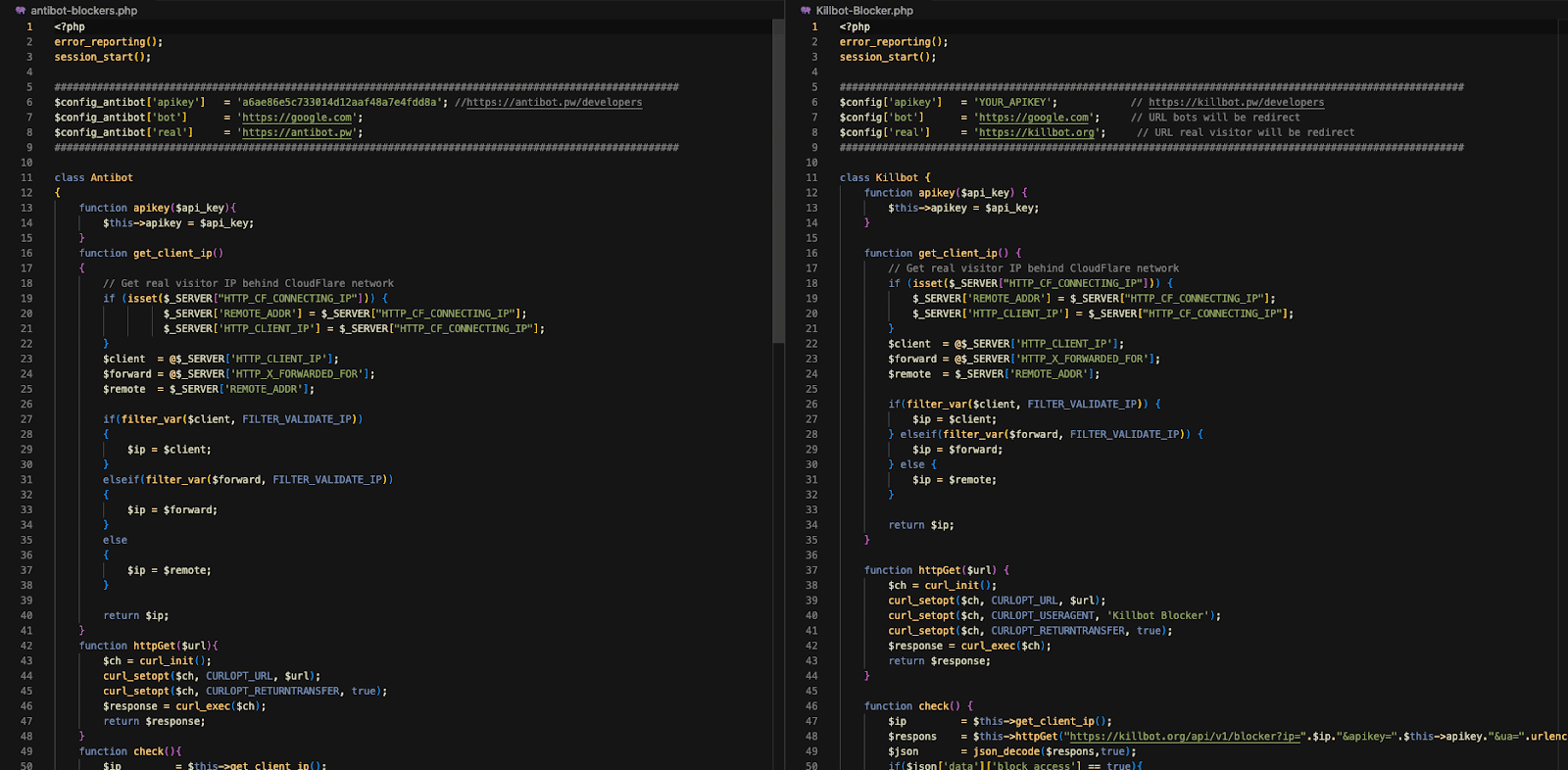
The two services serve their PHP scripts in similar ways, renaming them for download as .TXT files. Comparing the scripts shows near identical similarities:
3717b7c862057a5deb406cf747c4669e3f41d217ae66a22a80b0bfe225a731a5 antibot-blockers.txt
2982112157807645a1c964e70a44d2a23021d4a62537ad2266445125c8783e5e Killbot-Blocker.txt
Installations of Killbot-integrated sites may be observed in captured phishing pages and other scam and fraudulent websites, like those that can be found in urlscan.io:
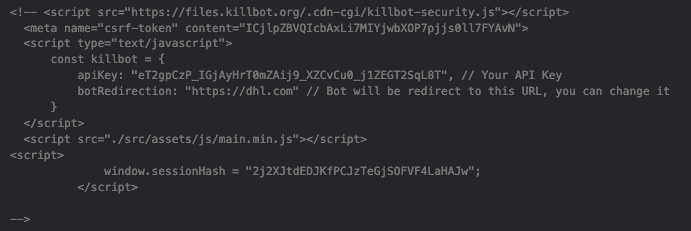
An example of client-side content used to integrate the Killbot service into a DHL phishing page is shown below. Filtered clients are redirected to the DHL home page:
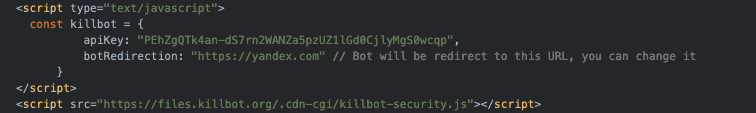
A similar setup is found in urlscan.io, showing activation using a published Killbot JavaScript including with a redirection for filtered clients to Yandex in this case.
Suspected developer/operator
In 2018, Deep End Research published an analysis of spam and phishing campaign activity centered around a community of operators based in Indonesia. The phishers notably targeted Apple, PayPal and other top brands, and utilized a number of utilities in their toolbox, including SendInbox, heart sender, GX40 sender, IndoXploit, and others. The community was found to be using tools believed to have been developed by Eka Syahwan. As noted in a 2020 post to Twitter, researchers identified a link between Syahwan and this Indonesian spam and phishing ecosystem. Also in 2020, a researcher posted a list of phishing kit URLs and their associated dropzone information to their blog. One of those kits was packaged in an archive named sendinbox-master.zip:
hXXp://lordnoob.hopto[.]org/gx40/sendinbox-master.zip
The exfiltration email recipient configured in this kit was ekasyahwan[@]hotmail.com, which is also the registrant email for the domain ANTIBOT.PW. As noted by Deep End Research, Syahwan is the developer of SendInbox. Syahwan is also the developer of Antibot, with the software project having been hosted on Syahwan’s @radenvodka GitHub account prior to being taken offline.
- Eka Syahwan, Indonesia
- ʀᴀᴅᴇɴᴠᴏᴅᴋᴀ (ᴇᴋᴀ ꜱ)
- @radenvodka (GitHub) – https://github.com/radenvodka
- https://id.linkedin.com/in/ekasyahwan
- Eka Syahwan – Chief Executive Officer (CEO) – CilegonTech
- Previously operated blog at http://www.ekasyahwan.com/
- Previously operated blog at http://blog.antibot.pw/
- Maintains business site for Cilegon Tech – Konsultan IT ((c) 2016) at https://cilegon-tech.blogspot.com/
- Chief Executive Officer: Eka Syahwan
- Also: cilegontech[.]com
- Maintains personal blog for RadenVodka at https://radenvodka-id.blogspot.com/
- Last post c.2018


Conclusion
Antibot has been a mainstay in various spammer and phishing circles as a bot traffic filtering script. A software project, originally hosted on GitHub, distributed the source code for Antibot and can be seen in active phishing page source content. The author and distributor of Antibot is suspected to be based in Indonesia in connection to local spam communities as an underground software/service provider specializing in phishing and bank fraud. Presently, ANTIBOT.PW is established as a platform with a web API and is offered as a commercial product and as a more refined service option under the name Killbot. What differentiates Antibot from other tools in the adversary toolbelt is the open-web-facing nature for which the service is presented. Contrast this to other tools and services generally sold and advertised via underground hacking forums. The operator of ANTIBOT.PW and Killbot wants to appear to be legitimate, despite a history of close involvement with unscrupulous communities and the development of software furthering criminal phishing and fraud activity within those communities. This is noted moreso when considering integrations and partnerships with other prominent phishing kits and services such as HijaIyh.
InQuest advises those looking to combat phishing and other fraudulent activity to remain aware of the presence of Antibot and Killbot in this ecosystem, and to consider websites integrating with their services to be likely related to criminal activity.
References
- http://www.deependresearch.org/2018/09/indonesian-spam-communities.html
- https://twitter.com/dave_daves/status/1234468103154798592
- https://twitter.com/dave_daves/status/1235528342130118657
- https://twitter.com/ninoseki/status/1250680128499101697
- https://twitter.com/malwrhunterteam/status/1342932154779639808
- https://aneilan.github.io/2020-11-24-crap-i-found.html
- https://blog.sucuri.net/2021/09/analysis-of-a-phishing-kit-that-targets-chase-bank.html
- https://www.joesandbox.com/analysis/282641/0/html
- https://www.blogger.com/profile/00594931846079630287
- https://github.com/radenvodka/antibot
- Project is now offline, but previously hosted source code for Antibot
- https://urlscan.io/result/79417576-9406-4f37-b3e1-251f8e56f64e/
- https://urlscan.io/result/5d85593b-e45d-49df-bfb3-a472a9a3f2de/
Appendix
Infrastructure
Domains:
- ANTIBOT.PW
- ANTIBOT.TECH
- ANTIBOT.XYZ
- KILLBOT.ORG
- KILLBOT.PW
Domain registrations:
- ANTIBOT.PW 2019-09-13 WEBCC domainesia.net Eka Syahwan [email protected]
- ANTIBOT.TECH 2019-12-23 Web Commerce Communications Ltd domainesia.net Privacy
- ANTIBOT.XYZ 2020-01-21 Web Commerce Communications Ltd domainesia.net Privacy
- KILLBOT.ORG 2020-04-17 CloudFlare, Inc. cloudflare.com Privacy
- KILLBOT.PW 2020-07-21 WEBCC cloudflare.com Privacy
Domain SOA records:
- antibot.pw. 1800 IN SOA ns1.domainesia.net. admin.domainesia.com. 2021072400 3600 1800 1209600 86400
- killbot.org. 1800 IN SOA kareem.ns.cloudflare.com. dns.cloudflare.com. 2310810561 10000 2400 604800 1800
- killbot.pw. 1800 IN SOA kareem.ns.cloudflare.com. dns.cloudflare.com. 2314410706 10000 2400 604800 1800
Hosting:
Hosting for services has been on VPS from Vultr (CHOOPA).
- 45.63.85.138 AS20473 | US | AS-CHOOPA
- 45.76.179.109 AS20473 | US | AS-CHOOPA
- 149.28.240.102 AS20473 | US | AS-CHOOPA
CDN service usage:
- The Killbot service (domains killbot[.]org, killbot[.]pw) are fronted by Cloudflare.
Hosts:
antibot.pw. 2855 IN A 149.28.240.102
killbot.org. 300 IN A 104.21.11.160
killbot.org. 300 IN A 172.67.166.105
killbot.pw. 300 IN A 104.21.35.84
killbot.pw. 300 IN A 172.67.216.54
antibot.pw. 1800 IN NS ns2.domainesia.net.
antibot.pw. 1800 IN NS ns1.domainesia.net.
killbot.org. 21600 IN NS kareem.ns.cloudflare.com.
killbot.org. 21600 IN NS kimora.ns.cloudflare.com.
killbot.pw. 21600 IN NS kareem.ns.cloudflare.com.
killbot.pw. 21600 IN NS kimora.ns.cloudflare.com.
Historical resolutions:
killbot.org 45.63.85.138 ip A 2021-08-07T20:40:53 2022-06-29T13:09:44
45.63.85.138 files.killbot.org domain A 2021-08-07T07:41:26 2022-06-10T17:25:44
45.63.85.138 go.killbot.org domain A 2021-08-07T07:41:27 2021-08-07T07:41:27
45.63.85.138 killbot.org domain A 2021-08-07T20:40:53 2022-06-29T13:09:44
45.63.85.138 killbot.pw domain A 2021-08-07T21:05:25 2022-06-28T13:32:45
45.76.179.109 antibot.pw domain A 2019-10-10T05:09:28 2020-04-16T02:11:26
45.76.179.109 files.antibot.pw domain A 2019-10-10T06:20:25 2020-04-16T04:22:09
45.76.179.109 xn--yp9h.antibot.pw domain A 2019-12-15T01:18:27 2019-12-15T01:18:27
45.76.179.109 www.antibot.tech domain A 2019-12-24T08:11:16 2020-05-12T20:47:26
45.76.179.109 antibot.xyz domain A 2020-01-21T10:48:30 2020-04-13T17:08:18
45.76.179.109 www.antibot.pw domain A 2020-04-14T16:04:11 2020-04-14T16:04:11
149.28.240.102 antibot.xyz domain A 2020-04-16T05:12:29 2021-01-19T08:19:47
149.28.240.102 antibot.pw domain A 2020-04-16T05:26:25 2023-07-14T11:26:51
149.28.240.102 files.antibot.pw domain A 2020-04-16T05:41:29 2023-07-09T21:40:19
149.28.240.102 rox.antibot.pw domain A 2021-07-24T14:16:26 2023-07-02T00:58:02
45.63.85.138 AS20473 | US | AS-CHOOPA
45.76.179.109 AS20473 | US | AS-CHOOPA
149.28.240.102 AS20473 | US | AS-CHOOPA
104.21.11.160 AS13335 | US | CLOUDFLARENET
172.67.166.105 AS13335 | US | CLOUDFLARENET
104.21.35.84 AS13335 | US | CLOUDFLARENET
172.67.216.54 AS13335 | US | CLOUDFLARENET
Files
PHP scripts:
3717b7c862057a5deb406cf747c4669e3f41d217ae66a22a80b0bfe225a731a5 antibot-blockers.txt
2982112157807645a1c964e70a44d2a23021d4a62537ad2266445125c8783e5e Killbot-Blocker.txt
The post Adversary On The Defense: ANTIBOT.PW appeared first on InQuest.
Source: Inquest
Source Link: https://inquest.net/blog/adversary-on-the-defense-antibot-pw/