
Recorded Futures Insikt Group has identified a large cluster of new infrastructure associated with usage of the custom Windows and Linux backdoor KEYPLUG, attributed to a highly-likely Chinese state-sponsored threat activity group tracked as RedGolf. RedGolf closely overlaps with threat activity reported under the aliases of APT41/BARIUM and reportedly has targeted US government entities. RedGolf has also reportedly boasted of connections to the the Chinese Ministry of State Security (MSS) and its members were previously linked to the Chengdu-based company Chengdu 404 Network Technology ().
RedGolf remains highly active within a wide range of geographies and is known to target aviation, automotive, education, government, media, information technology, and religious organizations. Organizations of strategic interest to the Chinese government and security services are likely at increased risk of targeting. This report examines recent activity of the group, tactics, techniques, and procedures, and offers mitigation strategies for organizations.
According to public reporting, RedGolf used a Linux version of the custom modular backdoor KEYPLUG to target US state government entities during 2021 and 2022. Insikt Group has identified a wider cluster of KEYPLUG samples and operational infrastructure used by RedGolf from at least 2021 to 2023. We actively track this malicious infrastructure using the term GhostWolf. Alongside KEYPLUG, we also identified RedGolf using Cobalt Strike, PlugX, and Dynamic DNS (DDNS) domains, all of which are commonly used amongst many Chinese state-sponsored threat groups. Insikt Group identified multiple infrastructure overlaps between publicly reported APT41/BARIUM campaigns across the identified GhostWolf infrastructure cluster.
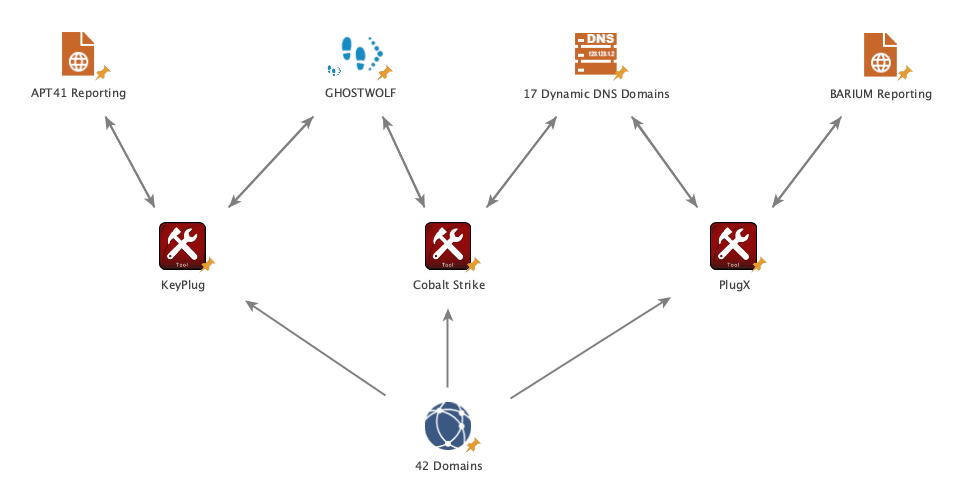 RedGolf infrastructure and TTPs (Tactics, Techniques, and Procedures) overlaps with APT41 and BARIUM. (Source: Recorded Future)
RedGolf infrastructure and TTPs (Tactics, Techniques, and Procedures) overlaps with APT41 and BARIUM. (Source: Recorded Future)
RedGolf will continue to target victims with KEYPLUG malware and its derivatives using command and control infrastructure spanning a variety of hosting providers. The group has previously utilized a mixture of both traditionally registered domains and DDNS domains, often featuring a technology theme. We believe this TTP will remain relatively unchanged with the exception of a decrease in DDNS use.
The employment of both Cobalt Strike and PlugX to target victim machines by Chinese state-sponsored threat activity groups, such as RedGolf, is highly likely to continue given the feature set provided by these tools, their ready availability, and the ability to obfuscate responsibility due to the number of other threat actors using these techniques.
Recorded Future proactively detects both Cobalt Strike and PlugX servers. We recommend incorporating this feed into blocking lists and/or alerting to prevent infections.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/with-keyplug-chinas-redgolf-spies-on-steals-from-wide-field-targets