Welcome back, aspiring cyberwarriors! As you are aware, traditional security approaches typically involve firewalls that either allow or deny traffic to specific ports. The problem is that allowed ports are visible to anyone running a port scan, making them targets for exploitation. Port knocking takes a different approach: all ports appear filtered (no response) to […]
The post Hacking with the Raspberry Pi: Getting Started with Port Knocking first appeared on Hackers Arise.
Welcome back, aspiring cyberwarriors!
As you are aware, traditional security approaches typically involve firewalls that either allow or deny traffic to specific ports. The problem is that allowed ports are visible to anyone running a port scan, making them targets for exploitation. Port knocking takes a different approach: all ports appear filtered (no response) to the outside world until you send a specific sequence of connection attempts to predetermined ports in the correct order. Only then does your firewall open the desired port for your IP address.
Let’s explore how this technique works!
What is Port Knocking?
Port knocking is a method of externally opening ports on a firewall by generating a connection attempt sequence to closed ports. When the correct sequence of port “knocks” is received, the firewall dynamically opens the requested port for the source IP address that sent the correct knock sequence.
The beauty of this technique is its simplicity. A daemon (typically called knockd) runs on your server and monitors firewall logs or packet captures for specific connection patterns. When it detects the correct sequence, it executes a command to modify your firewall rules, usually opening a specific port for a limited time or for your specific IP address only.
The knock sequence can be as simple as attempting connections to three ports in order, like 7000, 8000, 9000, or as complex as a lengthy sequence with timing requirements. The more complex your sequence, the harder it is for an attacker to guess or discover through brute force.
The Scenario: Securing SSH Access to Your Raspberry Pi
For this tutorial, I’ll demonstrate port knocking between a Kali Linux machine and a Raspberry Pi. This is a close to real-world scenario that many of you might use in your home lab or for remote management of IoT devices. The Raspberry Pi will run the knockd daemon and have SSH access hidden behind port knocking, while our Kali machine will perform the knocking sequence to gain access.
Step #1: Setting Up the Raspberry Pi (The Server)
Let’s start by configuring our Raspberry Pi to respond to port knocking. First, we need to install the knockd daemon:
pi> sudo apt install knockd
The configuration file for knockd is located at /etc/knockd.conf. Let’s open it.
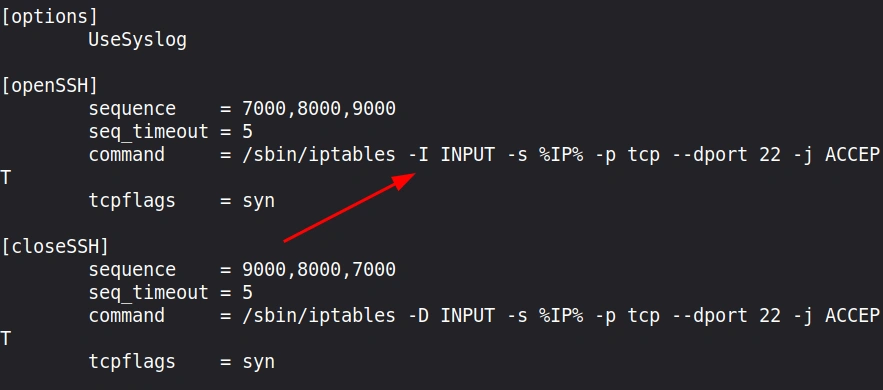
Here’s a default configuration that is recommended for beginners. The only thing I changed -A flag to -I to insert the rule at position 1 (top) so it will be evaluated before any DROP rules.
The [openSSH] section defines our knock sequence: connections must be attempted to ports 7000, 8000, and 9000 in that exact order. The seq_timeout of 5 seconds means all three knocks must occur within 5 seconds of each other. When the correct sequence is detected, knockd executes the iptables command to allow SSH connections from your IP address.
The [closeSSH] section does the reverse: it uses the knock sequence in reverse order (9000, 8000, 7000) to close the SSH port again.
Now we need to enable knockd to start on boot:
pi> sudo vim /etc/default/knockd
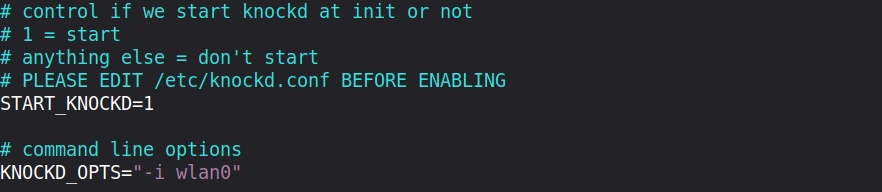
Change the line START_KNOCKD=0 to START_KNOCKD=1 and make sure the network interface is set correctly.
Step #2: Configuring the Firewall
Before we start knockd, we need to configure our firewall to block SSH by default. This is critical because port knocking only works if the port is actually closed initially.
First, let’s set up basic iptables rules:
pi> sudo apt install iptables
pi> sudo iptables -A INPUT -m conntrack –ctstate ESTABLISHED,RELATED -j ACCEPT
pi> sudo iptables -A INPUT -p tcp –dport 22 -j DROP
pi> sudo iptables -A INPUT -j DROP
These rules allow established connections to continue (so your current SSH session won’t be dropped), block new SSH connections, and drop all other incoming traffic by default.
Now start the knockd daemon:
pi> sudo systemctl start knockd
pi> sudo systemctl enable knockd
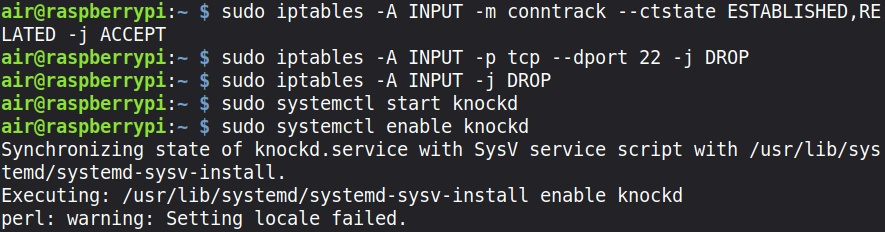
Your Raspberry Pi is now configured and waiting for the secret knock! From the outside world, SSH appears with filtered access.
Step #3: Installing Knock Client on Kali Linux
Now let’s switch to our Kali Linux machine. We need to install the knock client, which is the tool we’ll use to send our port knocking sequence.
kali> sudo apt-get install knockd
The knock client is actually part of the same package as the knockd daemon, but we’ll only use the client portion on our Kali machine.
Step #4: Performing the Port Knock
Before we try to SSH to our Raspberry Pi, we need to perform our secret knock sequence. From your Kali Linux terminal, run:
kali> knock -v 192.168.0.113 7000 8000 9000
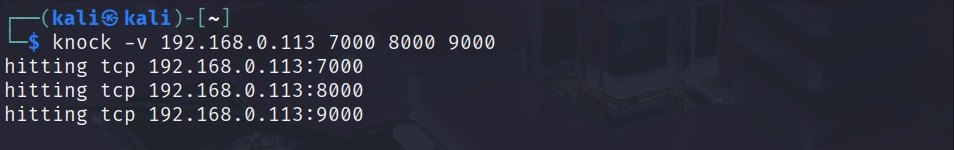
The knock client is sending TCP SYN packets to each port in sequence. These packets are being logged by the knockd daemon on your Raspberry Pi, which recognizes the pattern and opens SSH for your IP address.
Now, immediately after knocking, try to SSH to your Raspberry Pi:
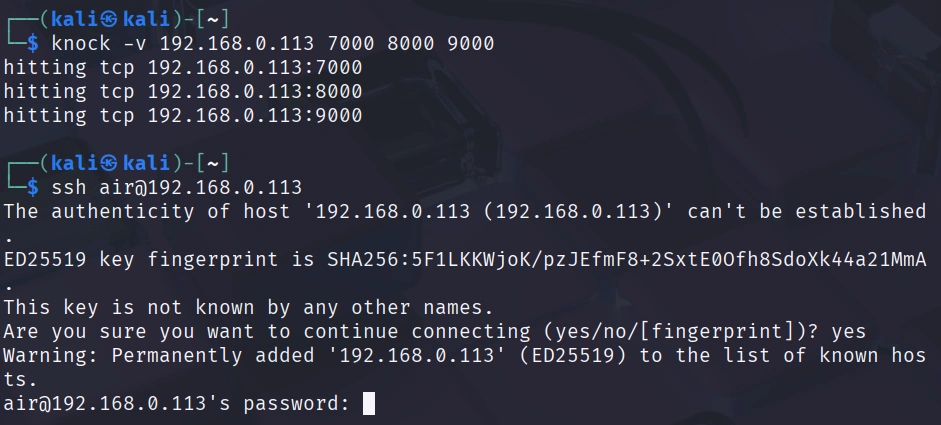
If everything is configured correctly, you should connect successfully! The knockd daemon recognized your knock sequence and added a temporary iptables rule allowing your IP address to access SSH.
When you’re done with your SSH session, you can close the port again by sending the reverse knock sequence:
kali> knock -v 192.168.1.100 9000 8000 7000
Step #5: Verifying Port Knocking is Working
Let’s verify that our port knocking is actually providing security. Without performing the knock sequence first, try to SSH directly to your Raspberry Pi:
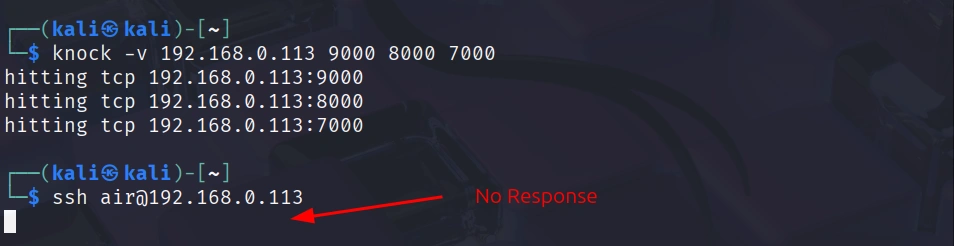
The connection should hang and eventually timeout. If you run nmap against your Raspberry Pi without knocking first, you’ll see that port 22 appears filtered:
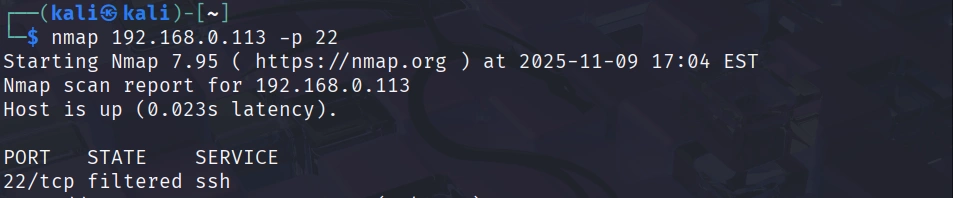
Now perform your knock sequence and immediately scan again:
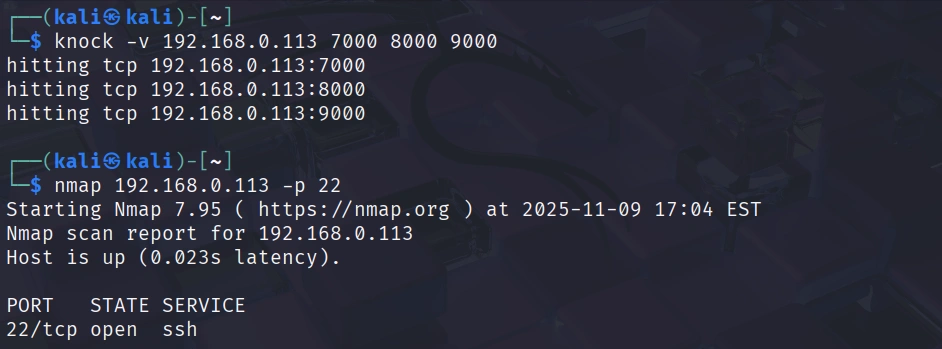
This demonstrates how port knocking makes services filtered until the correct sequence is provided.
Summary
Port knocking is a powerful technique for adding an extra layer of security to remote access services. By requiring a specific sequence of connection attempts before opening a port, it makes your services harder to detect to attackers and reduces your attack surface. But remember that port knocking should be part of a defense-in-depth strategy, not a standalone security solution.
The post Hacking with the Raspberry Pi: Getting Started with Port Knocking first appeared on Hackers Arise.
Source: HackersArise
Source Link: https://hackers-arise.com/hacking-with-the-raspberry-pi-getting-started-with-port-knocking/