Microsoft has released security updates for 131 vulnerabilities and a disclosure for one yet-unpatched vulnerability for its July 2023 Patch Tuesday rollout: 9 are rated as Critical while the remaining 122 are rated as Important. There is one vulnerability without a severity rating.
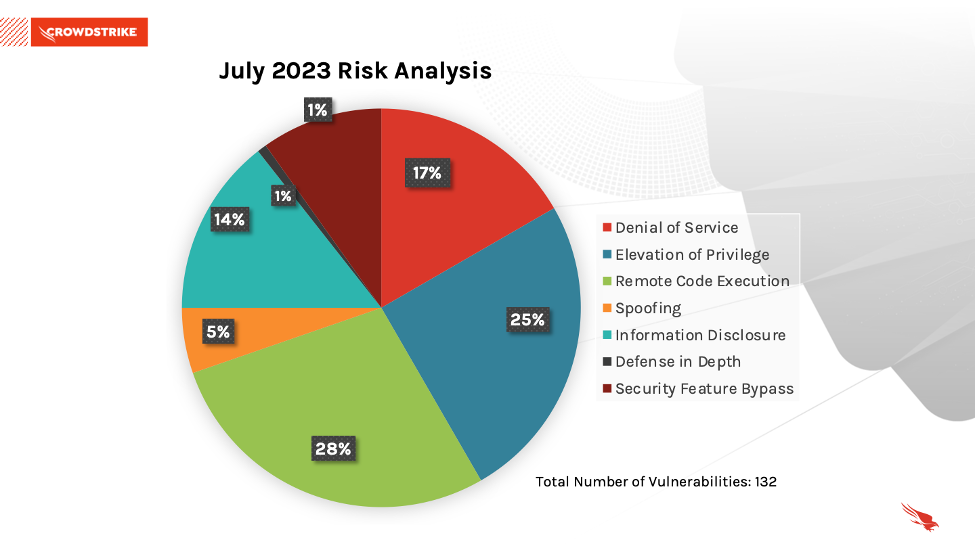
July 2023 Risk Analysis
This month’s leading risk type is remote code execution (28%), followed by elevation of privilege (25%) and denial of service (17%).
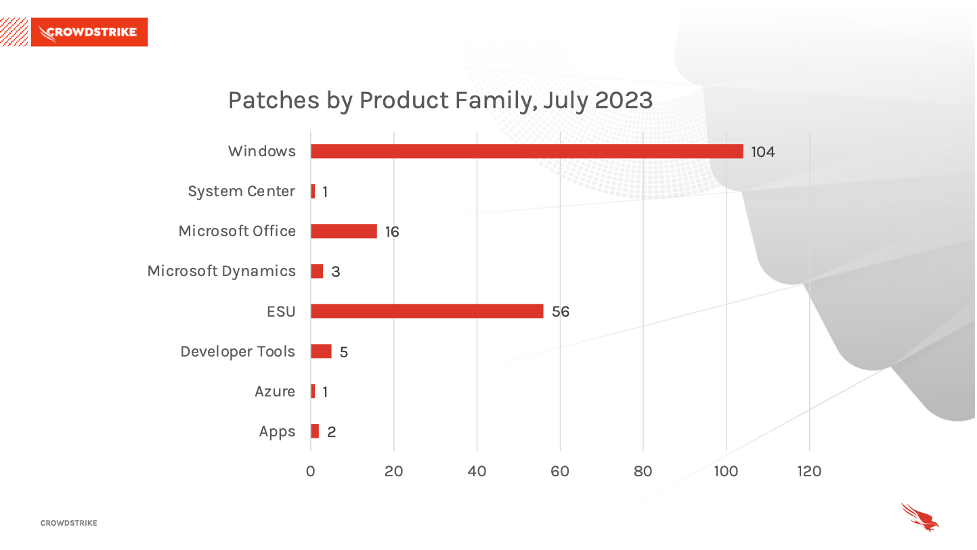
The Microsoft Windows product family received the most patches this month with 104, followed by Extended Support Updates (56) and Microsoft Office products (16).
Actively Exploited Zero-Day Vulnerability Affects Office and Windows HTML
Microsoft Office and Windows has disclosed an unpatched and Important-rated vulnerability CVE-2023-36884, which has a CVSS of 8.3. Microsoft has released guidance on this unpatched remote code execution vulnerability impacting Windows and Office products. Microsoft states, “Microsoft is investigating reports of a series of remote code execution vulnerabilities impacting Windows and Office products. Microsoft is aware of targeted attacks that attempt to exploit these vulnerabilities by using specially-crafted Microsoft Office documents.” The Microsoft Threat Intelligence team has released a blog summarizing the findings and tools, TTPs and recommendations needed to defend against these attacks.
| Rank | CVSS Score | CVE | Description |
| Important | 8.3 | CVE-2023-36884 | Office and Windows HTML Remote Code Execution Vulnerability |
Table 1. Zero day in Microsoft Office and Windows HTML
Actively Exploited Zero-Day Vulnerability Affects Windows MSHTML Platform
Microsoft Windows MSHTML has received a patch for CVE-2023-32046, which is rated Important and has a CVSS of 7.8. This vulnerability could allow an attacker to gain user access to the affected application by sending a specially crafted file via email or web. User interaction is required for successful exploitation. Microsoft recommends, “To stay fully protected, we recommend that customers who install Security Only updates install the IE Cumulative updates for this vulnerability.”
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2023-32046 | Windows MSHTML Platform Elevation of Privilege Vulnerability |
Table 2. Zero day in Windows MSHTML platform
Actively Exploited Zero-Day Vulnerability Affects Windows SmartScreen
A patch has been released for CVE-2023-32049, a security feature bypass vulnerability in Microsoft Windows SmartScreen that is rated Important and has a CVSS of 8.8. This vulnerability allows for an adversary to bypass the Open File Security Warning prompt when a file is downloaded or opened via the internet. User interaction is required in order to successfully exploit this vulnerability.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2023-32049 | Windows SmartScreen Security Feature Bypass Vulnerability |
Table 3. Zero day in Windows SmartScreen
Actively Exploited Zero-Day Vulnerability Affects Windows Error Reporting Service
Microsoft Windows Error Reporting Service is receiving a patch for CVE-2023-36874, which is rated Important and has a CVSS of 7.8. Microsoft states that an attacker must have local access to the machine with default user privileges in order to successfully exploit the flaw and gain administrative privileges.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2023-36874 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
Table 4. Zero day in Windows Error Reporting Service
Actively Exploited Zero-Day Vulnerability Affects Microsoft Outlook
Microsoft Outlook is receiving a patch for Important-rated vulnerability CVE-2023-35311, which has a CVSS of 8.8. This vulnerability resides in the Outlook Security Notice Prompt, allowing for an attacker to bypass. Microsoft states that the Preview Pane is an attack vector for this vulnerability and user interaction is required.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2023-35311 | Microsoft Outlook Security Feature Bypass Vulnerability |
Table 5. Zero day in Microsoft Outlook Security
Critical Vulnerabilities Affect Windows
CVE-2023-35315 is a Critical vulnerability affecting Windows Layer-2 Bridge Network Driver with a CVSS of 8.8. Microsoft says, “An unauthenticated attacker could exploit the vulnerability by sending a specially crafted request to a Windows Server configured as a Layer-2 Bridge.” To successfully exploit this vulnerability, an attacker must first gain access to the restricted network prior to launching an attack.
CVE-2023-35352 is a Critical vulnerability affecting Windows Remote Desktop with a CVSS of 7.5. Microsoft states that this vulnerability is more likely to be exploited. If the vulnerability is successfully exploited, an adversary would be able to bypass authentication using certificates or private keys when initiating a remote desktop session.
CVE-2023-35365, CVE-2023-35366 and CVE-2023-35367 are Critical vulnerabilities affecting Windows Routing and Remote Access Service (RRAS), and each has a CVSS score of 9.8. These vulnerabilities are only exploitable on Windows servers that have Routing and Remote Access Service (RRAS) roles, which are not installed and configured by default. Microsoft states, “… to exploit this vulnerability, an attacker would need to send specially crafted packets to a server configured with the Routing and Remote Access Service running.”
CVE-2023-32057 is a Critical vulnerability affecting Microsoft Message Queuing (MSMQ) with a CVSS of 9.8. In order to successfully exploit this vulnerability, an attacker would have to send a specifically crafted malicious MSMQ packet to a MSMQ server, leading to a remote code execution. This Windows component needs to be enabled for a system to be vulnerable. Microsoft recommends checking if “Message Queuing” service is running and TCP port 1801 is listening on the machine.
CVE-2023-35297 is a Critical vulnerability affecting Windows Pragmatic General Multicast (PGM) with a CVSS of 7.5. Microsoft states,“This attack is limited to systems connected to the same network segment as the attacker. The attack cannot be performed across multiple networks (for example, a WAN) and would be limited to systems on the same network switch or virtual network.” With a high attack complexity, an attacker must perform additional actions beforehand.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2023-35315 | Windows Layer-2 Bridge Network Driver Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2023-35352 | Windows Remote Desktop Security Feature Bypass Vulnerability |
| Critical | 9.8 | CVE-2023-35365 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-35366 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-35367 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-32057 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2023-35297 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
Table 6. Critical vulnerabilities in MS Windows
Guidance on Microsoft Signed Device Drivers Being Used Maliciously
Microsoft was recently alerted to the malicious exploitation of drivers certified through its Microsoft Windows Hardware Developer Program (MWHDP) in post-exploitation activities. These attacks involved the adversary obtaining administrative privileges on compromised systems and subsequently utilizing the compromised drivers. Microsoft has immediately suspended the developer accounts involved in this incident. Microsoft services are not affected by this issue, according to its investigation. The company recommends that all customers install the latest Windows updates and ensure antivirus and endpoint detection products are up-to-date. Please see the Microsoft Security Advisory for more information.
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched. As is the case for the ProxyNotShell vulnerabilities, it’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization’s methods for cybersecurity and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of security events every day from across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
Learn more about how CrowdStrike Falcon® Spotlight vulnerability management can help you quickly and easily discover and prioritize vulnerabilities here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- See how Falcon Spotlight can help you discover and manage vulnerabilities and prioritize patches in your environments.
- Learn how CrowdStrike’s external attack surface module, Falcon Surface, can discover unknown, exposed and vulnerable internet-facing assets enabling security teams to stop adversaries in their tracks.
- Learn how Falcon identity protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent.
Source: CrowdStrike
Source Link: https://www.crowdstrike.com/blog/patch-tuesday-analysis-july-2023/