Bridging the communication gap between security practitioners and executives
Businesses must navigate numerous obstacles, from workplace changes to pandemics and wars. However, it's important to distinguish between actual threats and potential risks. Organizations need a durable advantage to identify and classify these challenges, and Intelligence plays a crucial role in evaluating risks and determining the appropriate response.
In business, the distinction between threats and risks may be clear, but in my experience, there is nuance in the analysis and final classification.
To simplify the path from intelligence to risk (I2R), in the summer of 2022, my Recorded Future colleagues (Dylan Davis, David Carver, and Harry Matias) and I sat down with a whiteboard to formalize our process. The below pyramid is how we think about identifying, managing, and communicating risks.
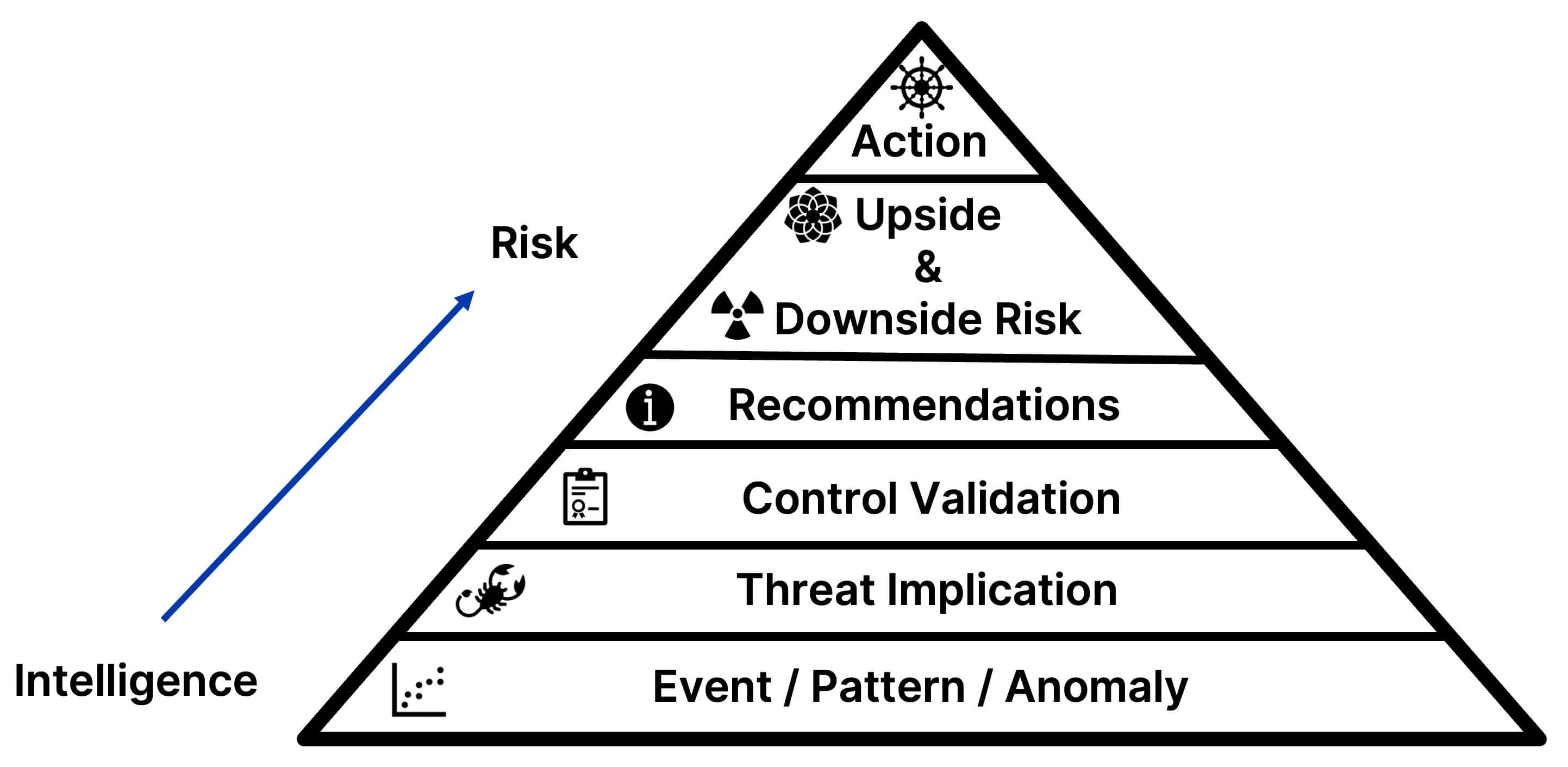
Connecting intelligence to risk and executive relevance is not straightforward. One of the biggest challenges businesses face is complexity. With so much information available, it can be difficult to determine what is relevant and what is not. This complexity can lead to the shadow of executive irrelevance, where leaders cannot make sense of the information they have and make informed decisions.
To overcome this complexity, businesses need broad visibility across different events. This is what Recorded Future's President, Stu Solomon, calls Foundational Intelligence. It's a process of gathering and analyzing data from multiple sources to comprehensively understand the current environment. By understanding the different types of events that are happening and how they are related, businesses can better evaluate the risks they face.
The next step in the process is threat implication. This is where analysts earn their paychecks. The skill of identifying non-obvious and perhaps non-intuitive implications is what sets good analysts apart from great ones. It can be mentally taxing, but the results are valuable. A broad background in geopolitics and cyber, as well as knowledge of current events, is a prerequisite for identifying threat implications. This step is where an answer takes shape for the two fundamental executive questions: "So what?" and "Now what?"
Control validation is the next step, where businesses determine if their controls are working as intended. When threats become technical, such as new malicious code, it's often discovered that controls are not functioning properly. This stage moves a threat from general thesis applicability to the exposure of a potential control gap or the reaffirmation that controls are functioning well. To properly understand internal controls, multiple individuals from across an organization are often required to provide input.
The "Recommendations" step is necessary for leadership to consider options, each presenting different risks. Ideally, this step produces one strong short-term and long-term recommendation coupled with a business justification that includes resource trade-offs. The next step is "Upside and Downside Risk.", which involves articulating residual risk from the preceding recommendations. Most enterprises prefer to qualify risk using the likelihood of occurrence and impact paradigm. Once the downside risk is measured (however imprecisely), upside risk is a crucial counterbalance thats often overlooked.
Finally, the Action pinnacle is when a business leader or leadership team decides to act, or not act (which is also a valid outcome) based on an articulation of the I2R steps and an understanding of current business focus and constraints.
Our desire is for this framework to bridge the communication gap between security practitioners and executives. Connecting intelligence to risk for an executive audience is a challenging process. We think this is a practical tool to help the worlds intelligence professionals and business leaders.
Download the whitepaper to learn more about the I2R framework and examples.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/introducing-intelligence-to-risk-pyramid