Guest post by Dr Anton Chuvakin, Senior Staff Security Consultant, Office of the CISO, Google Cloud.

If you wake up an average security professional at 3AM and ask them “hey, what is security about?”, a large majority would say “it is about the threats.” Ultimately, security (whether “cyber” or “information”) is unthinkable without the threats. Security professionals are meant to defend against threats from criminals, insiders, and nation-states.
However, if you see the same security person at 9AM, you will likely find that this is not what they actually do most of their day. They configure tools, clean up user messes, write reports, deal with auditors, etc. Sure, some of the activities may be indirectly helpful and perhaps even implicitly informed by the threats, the majority really are not.
So why does everybody seem to support threat-centric security conceptually, but few practice it operationally?
WHAT IS IT?
First, what is it? To me, a very reasonable definition is: “Threat-informed defense is the systematic application of a deep understanding of adversary tradecraft and technology to improve defenses.” (source: MITRE Engenuity Center for Threat-Informed Defense) This seems very logical, and very defensible, and ultimately does not over-focus on threat intelligence (TI).
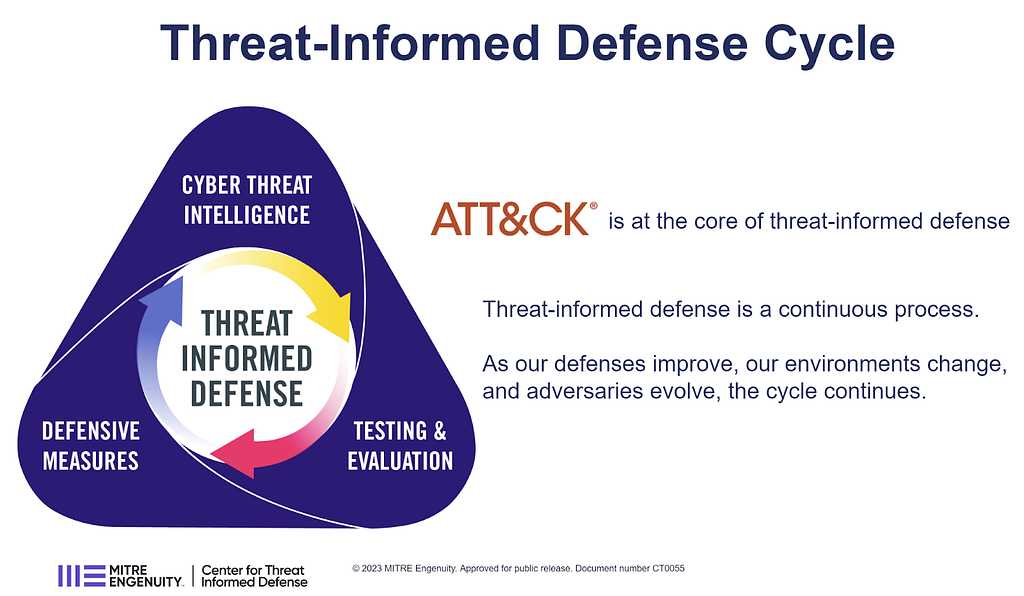
Critically, threat-informed is not about “get as much cyber threat intel (CTI) as possible, then very proudly do nothing.” This is really not about the CTI as such, but about making decisions informed with threat … here I struggle for the right word … knowledge? Information? Thinking?
Next, why is there a disconnect? Exploring this via social media led to many curious responses.
WHY NOT DO IT?
There are several possible explanations for this disconnect
- To start, one can say that foundational levels of security are not and perhaps even should not be threat-centric. After all, much of basic security is just good engineering, no? Threat-informed defense should be built upon foundational cyber-hygiene.
- Further, even in 2023, many organizations have not built the security basics and so their next 3 steps in their security journey are necessarily not threat-informed (they are moving from the hypothetical Basics Level 1 to Basics Level 3, whatever those are).
- Ironically, the “cyber-havenots” are less likely to practice threat-informed security while they are the ones who can benefit the most from focusing their scarce resources on threats that matter! Basics matter, but basics prioritized by real threats are better!
- I’ve met people with genuine belief that good security should not be threat-informed (!) — think of a (dated) example of application whitelisting that, when configured brutally enough, works against any and all threats.
- Poor quality of threat intel makes organizations unwilling and unable to make decisions off their collected threat data. Threat intelligence is often incomplete, inaccurate, or outdated, and this makes it difficult for organizations to make informed security decisions.
- Outside of security, immature IT capabilities ruin threat-informed defense. If your IT asset management, change management, etc. are inflexible, silo’d, hostile to security, your defenses can probably only be static and unchanging.
- Sometimes, the bridge from threat intelligence to security controls isn’t conceptualized, built or practiced. The organizations have threat intel in one bucket, and their security controls in another.
- Organizations also lack the types of personnel that can turn threat knowledge into improved defenses or drive threat-informed changes to defense approaches they practice.
- Compliance culture is focused on building static, auditor-proof defenses. A shift in security culture is often required to adopt a threat-informed approach and this is hard for many organizations, large or small.
- Narrow use case around threats: organizations only practice threat-informed detection, but not the rest of security.
OK, so many organizations are not practicing threat-informed security, what can be done about it? Actually, let’s discuss the scope of this first.
WHAT SHOULD BE THREAT-INFORMED?
As we mentioned above, there are some organizations that treat “threat-informed” very narrowly and equate it with “gather TI / CTI” or “use TI / CTI for detection.” Ultimately, very few people would argue that threat detection without threat knowledge can ever work.
However, how about patching and broader vulnerability management? Network security and network architecture? Application security? Various GRC and such?
I suspect in a lot of these areas we are missing the opportunity to insert the threat thinking.
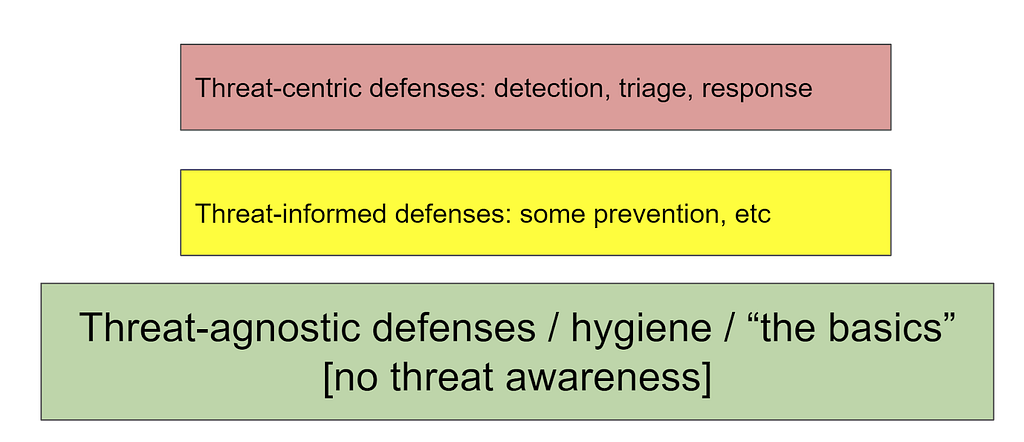
The diagram above starts to build an answer that we plan to explore in the future blogs.
HOW TO BE [MORE] THREAT-INFORMED?
How to embark on this journey? First, let’s talk about prerequisites for introducing more threat -informed thinking (and doing!) into your security.
Pre-requisites
- Some security maturity; a shared understanding that some thin layer of security basics has been in place and the improvements to the foundational security controls are practiced.
- Some IT maturity mostly in the areas of asset and change management, and IT operations resilience.
- Some threat awareness, some threat intelligence collection and use practices (an easy prerequisite to make as most security products use threat intelligence for various tasks)
Lacking these prerequisites implies that the organization is not ready to engage with threat-informed defense.
WHERE DO WE GO FROM HERE?
In further blogs, we will dive deep into “what is threat-informed defense?” (part 2), “getting started with threat-informed defense” (part 3), and continue with a series of special topics and use cases related to threat-informed defense.
Threat-informed Defense Is Hard, So We Are Still Not Doing It! was originally published in MITRE-Engenuity on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post Threat-informed Defense Is Hard, So We Are Still Not Doing It! appeared first on Security Boulevard.
Anton Chuvakin
Source: Security Boulevard
Source Link: https://securityboulevard.com/2023/08/threat-informed-defense-is-hard-so-we-are-still-not-doing-it/